Security in A-IMS
Zhang Shiwei Ni Na
(Central Academy of ZTE Corporation, Nanjing 210012, China)
Abstrac t:The Advances to IP Multimedia Subsystem(A-IMS)architecture,based on the 3rd Generation Partnership Project 2(3GPP2)'s Multimedia Domain(MMD),integrates all the service functions based on the Session Initiation Protocol(SIP)of the IP Multimedia Subsystem(IMS)and Multimedia Domain(MMD).Moreover,it supports the non-SIP applications.As for network operation,the A-IMS architecture makes some extension and supplement to the security of the IMS/MMD network,such as the addition of Security Operation Center(SOC)and posture agent,which greatly improves the security of the IMS/MMD network.The research of A-IMS is still in the stage of framework description,and still has many unclear details such as terminal support for the posture agent,content of the security information exchange,and definition of security policy,which ask for further research.
T he Advances to IPMultimedia Subsystem(A-IMS)[1]is a mobile multimedia service system,which was released by Verizon Wireless,the second largest mobile operator in the USA,along with its suppliers Cisco,Lucent,Motorola,Nortel and Qualcomm,in July 2006.Based on the 3rd Generation Partnership Project 2(3GPP2)'s Multimedia Domain(MMD),the A-IMSarchitecture not only integrates all the service functions based on the Session Initiation Protocol(SIP)of the IPMultimedia Subsystem(IMS)and Multimedia Domain(MMD),but also supports the non-SIPapplications.As for network operation,it makes some extension and supplement to the security of the IMS/MMD network,such as the addition of the Security Operation Center(SOC)and posture agent.
1 Service Functions Supported by A-IMS
The A-IMSnot only inherits all the service functions from the IMS/MMD,but also makes enhancement and extension in security,mobility,policy,Quality of Service(QoS),peering,accounting,legal monitoring,emergency call and presence.
2 A-IMS System Architecture
Figure 1 shows the A-IMSsystem architecture.Its major Network Elements(NE)are the IPGateway(IPGW),Bearer Management(BM),Application Management(AM),Policy Management(PM),Security Management(SM),Service Broker(SB),Service Data Management(SDM)and Access Terminal(AT).The SM,PM,BM,IPGW and ATare related to security.
Although the names of the A-IMS NEs are different from those of the IMS NEs[2]of 3GPPand MMDNEs[3]of 3GPP2,the A-IMSNEs,except SM,are parallel to the IMSNEs defined by 3GPP,3GPP2,and even TISPAN[4].For example,the AM,SDM and PM are corresponding to the Call Session Control Function(CSCF),Home Subscriber Server(HSS)and Policy Decision Function(PDF)in the IMS,respectively.As the core of the SOC,the SM is responsible for collecting the information of security events in the A-IMSNEs,completing intrusion detection,controlling equipment operation,and distributing security policies.It is also in charge of the posture evaluation for mobile teminals.According to the compatibility between terminals and network equipment,it decides whether the terminals are allowed to access,and which kinds of services they can enjoy.
3 Security threats to IMS
The security threats to the IP-based IMS system include the following:
(1)Detection Threat
Through scanning the network's topology,hackers can identify easy-to-attack devices without hassle.
(2)DDoSAttack
Distributed Denial of Service(DDoS)is the most dangerous attack to the current IPnetwork.It can cause any high-performance system to crash.The A-IMSpays special attention to solutions to the detection and prevention of this kind of attack.
(3)Interrupting and Taking over Equipment
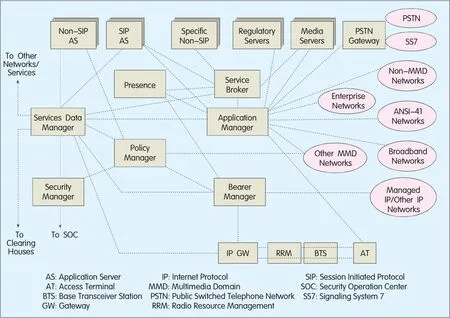
▲Figure 1. A-IMS system architecture.
This attack belongs to the broker attack.Usually,it illegally accesses the special devices(by means like illegally adding a route into the routing table)along with detection.
(4)Illegal Service Use and Service Fraud
This means the unauthorized use of network resources.
(5)Zero Day Attack
It attacks the network on some specialday.
(6)Stealing Private Information from Host or AT
It is the behavior of collecting private information from the ATby spy software and malicious programs,including transferring personal information,eavesdropping SIPcalls,and recording and reporting service use ratios.
The A-IMSimproves the security mechanism in IMS/MMD,adds new NEs like the SM,and establishes a new security system.It realizes the prevention,monitoring and control of attacks.
4 A-IMS Inherits IMS's Security System
The A-IMSinherits allthe security characteristics of theIMS/MMD,such as authentication,encryption and the protection algorithm for data integrity.Therefore,it has the same algorithms with the IMS/MMD in legality checking for SIP users,and the data privacy and integrity[5-7].Moreover,the algorithms have considered the support to the non-SIPapplications.(A-IMS's inheritance from the IMSsecurity system mentioned in this paper refers to its succession of the authentication and encryption mechanism,however,there are some changes in detail.)
(1)Authentication Algorithm There is Lay-2 initial access authentication,IPmobile service authentication and SIPapplication authentication in the A-IMSsystem.Moreover,the authentication is necessary for secure communications between NEs.The A-IMShas different authentication algorithms for integrated devices and non-integrated devices.For integrated devices,the A-IMSemploys 3GPP2 Authentication and Key Agreement/IPSecurity(AKA/IPSec)to SIPapplication,while using specific authentication protocols to non-SIPapplication,such as Transport Layer Security(TLS).
For non-integrated devices,it uses 3GPP2 AKA/IPSec or TLSto SIPapplication,while also adopting specific authentication protocols to non-SIPapplication such as TLS.
(2)Encryption and Data Protection
The A-IMSalso uses the encryption and data integrity algorithms,as shown in Table 1.
5 A-IMS Security System Enhancement
Compared with the IMS,the A-IMS enhances the integrated security and unified security management,SOC,device admission control,and security policies.
5.1 Integrated Security and Unified Security Management
Since the A-IMShas to handle network traffic at Gigabit rates,it integrates security mechanism into every NEin the system to avoid the network“bottleneck”.The NEs dispersed in different locations can work under unified security policies by the SOC distributing the policies and by the SM checking security events.In this way,unified security management in the entirenetwork is fulfilled.For instance,the SOC can use the integrated security mechanism to distribute the security policies like the traffic standard to every NE,identify,distinguish and trace any abnormal behavior through local and remote measurements,and then quickly block the spread of viruses.This unified integrated security mechanism greatly improves the security of the entire system compared with that of the IMS/MMD.
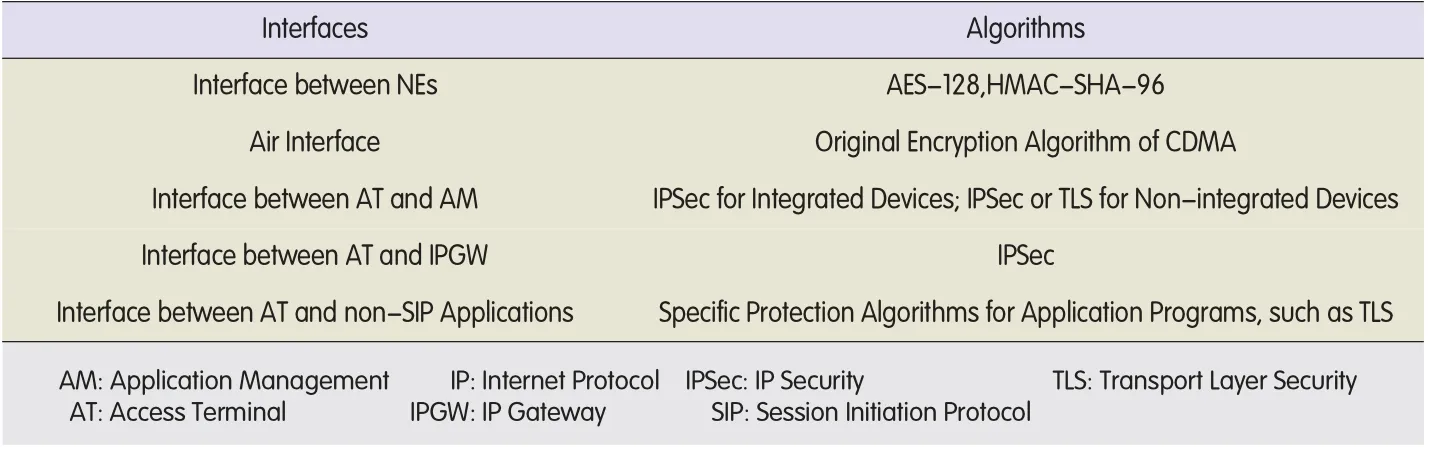
▼Table 1. Algorithms used between various interfaces in A-IMS
5.2 SOC
The SOC,mainly used in centralized monitoring,reporting and processing,is the most important entity newly added into the A-IMS,and is the core of security management of the entire system.It,through making and distributing policies,collects the security information from the NEs like AM,checks service status,and identifies,analyzes and handles outside intrusions.It provides mature and robust protection to the A-IMS.Besides,the SOC has the capabilities of accident management and judicial investigation assistance,which helps crisis handling.
Since the SOC is crucial for the security of the entire network,it is usually necessary to use redundant devices and Uninterruptible Power Supply(UPS)for the reliability of SOC hardware.Moreover,the authorization of SOC operators should be clearly defined,and nobody except authorized persons can log in the SOC.Background monitoring should also be conducted for operations of any SOC operators,and careful auditing on the security rules of internal information of the SOC is a must to ensure its normal operation.
5.3 Device admission control
Device admission control is a kind of network behavior that decides if the terminal is allowed to access the network.Moreover,it determines the service levels for the accessed terminals according to their security postures.
The A-IMSclassifies terminals into three types:the voice-only closing terminal,the advanced terminal supporting voice and data,and the personalcomputer with EV-DO ability.The last two are Intelligent Agent Technology(IAT)terminals,and are the major objects of device admission control of the A-IMS.
Device admission control is a major part for security enhancement.The access control measures,such as authorization and encryption,are used to implement device admission control in the A-IMSnetwork.Moreover,the A-IMS has a new function of security agent that can verify the security status of the AT and determine the security level for its access.If the security agent runs in the IAT,it is called Posture Agent(PA);if it works in such network devices as the AM and BM,it is Mobile Security Agent(MSA).
5.3.1 PA
The PA in the IATis an important part for device admission control.It collects the posture information about the AT(including if the version of the operating system is authorized,and whether it has patched correctly),and sends the results to the SM through the IPGW.
In an initial IATaccess,the SM checks the information report of the device posture sent by the PA,and,according to the related security policies,decides an initialpolicy corresponding to the IPGW:a limited or a full access.If it is a limited access,the related security policies will download to the BM so that the devices connect to the SIPservice port for emergency call handling on a specific AM only through the BM.Moreover,Web traffic willbe transferred to the update server that asks users to download the updated software.
The benefits of the device admission control based on the PA are the following:
·It ensures the consistency of security policies between user equipment and the network,and prevents worms,viruses,and spy and malicious software in advance.It helps operators pay more attention to the precaution rather than be busy in handling security events,which greatly improves the security of the A-IMS network.
·It offers a measure for checking and controlling the ATconnected to the network with no need to consider the specific access modes.This improves the adaptation capability and scalability of the network.
·It refuses incompatible and uncontrollable terminal devices,avoiding any impact on network availability.
·It can reduce the operational payment caused by the identification and repair of incompatible,unmanageable and infected systems.
·It protects vulnerable,incompatible and uncontrollable terminal devices from attacks,which also improves the availability of the network.
5.3.2 MSA
The MSA,which lies on the NEs like the AM and BM,cooperates with the PAto implement the function of device admission control.Moreover,it can monitor equipment status according to the requirements of the SM,assist the SM in checking and removing threat of“Zero Day”,and reduce the maintenance cost in system attack repair,which is very important when multiple access modes exist in the network(like WiFiand broadband access).With the capability of reverse firewall,the MSA can analyze the behavior during checking threats rather than only relying on users'signature,which is very important for preventing the“Zero Day”attack.
The MSA has all the functions the PA has.In addition,it has the following functions:
·Host intrusion prevention
·Blocking the spy ware
·Preventing buffer overflow attack
·Providing capability of distributed reverse firewall
·Stopping malicious mobile code intrusion
·Ensuring the integrity of the operating system
·Auditing the log
·Enhancing QoSapplication
5.4 Security Policies
The security policies are those that the SOC asks the system to run automatically when a security event happens in the network.
5.4.1 Hierarchy of Security Agents
The security policies play an important role in the A-IMS.By them,the SM can implement security management,DDoS prevention,access control,intrusion prevention,authorization and device admission control.The SM uses a built-in Mobile Security Agent Major Controller(MSA-MC)to control the MSAs of other NEs.
The MSA in the IATcollects the information about the host,and then sends the information to the MSA-MC.According to the related policies,the MSA-MC preprocesses the relevant information,and sends the results to the Home Security Management(H-SM),where the SM will make posture evaluation and abnormalbehavior checking,and determine a security level for the access.
5.4.2 Multi-level Management Model of SOC
With the SOC,the A-IMSfulfills multi-level policy control.The national SOC distributes security policies to local SMs,implementing the unified security management in the entire network.
5.5 Precaution of DDoS
The A-IMSemploys the self-learning algorithm to prevent DDoS.The algorithm can learn the traffic modelto adapt itself to a special network condition.For example,it can learn SIPbehavior to determine a proper traffic threshold.The A-IMScan distinguish legal,suspected and malicious traffic,and only legal traffic is allowed to pass its NEs.
The function of DDoSprecaution usually runs in an unremarkable background model.When the system is suspected to be attacked,the traffic diversion mechanism will be activated to redirect traffic to the protection system for analysis and control,and then return legitimate traffic to the network.
5.6 Security Log and Report
All the A-IMSNEs,including AM,BM,IPGW,APand SDM,support standard registration and report of security events.The warning of security events will be sent to the security incident management subsystem to conduct persistent storage,analysis and auditing.The subsystem,as a log collection station,employs near real-time transmission to implement real-time monitoring of security operations.
The A-IMSlog transmission is based on the IPFlow Information Export(IPFIX)protocol,Security Device Event Exchange(SDEE)protocol,Simple Network Management Protocol version 3(SNMPv3)and Syslog protocol.
6 Conclusions
In the IMS/MMD,the network security is divided into intra-domain security and cross-domain security.The former is further subdivided into access security and core network security.The A-IMS improves the access security by introducing the mechanisms such as PA,MSA,two-way firewall and IDS/IPS,while it employs the policy-based centralized security management mechanism that makes every NEin the control of the central SOC and greatly enhances the core network security.Generally,compared with the IMS/MMD,the A-IMSgreatly improves the intra-domain security.As for the cross-domain security,the A-IMS inherits the original mechanism of the IMS/MMD and uses the IPSec to implement the cross-domain communication encryption.
Overall,the security mechanism of the A-IMSis stronger then that of the IMS/MMD.
(1)The SOC/SM is introduced into the A-IMSfor multi-level security management of the network,which fulfills the integral and centralized control of system security.
(2)The A-IMSproposes the concept of security policy.The security policies help implement the automatic controlof network security.
(3)The A-IMSemphasizes the unified security management of the overall system.It integrates security management into every NE.The SM collects and analyzes security events in the NEs,and makes proper handling according to the security policies.
(4)The A-IMSemploys two-way firewall and IDS/IPSto protect both the network and terminals from being attacked.
(5)The A-IMSproposes the concept of PA and MSA.The PA is set up in the IATfor checking the version and patches of the operating system and firewall of terminals.This enforces terminals to reach the security level required by the network.
The A-IMSstands for the research direction of the IMSsecurity.However,the A-IMSstandardization is still in the stage of network framework description,and has many unclear details such as terminals'support(compatibility)of PA,content of exchanged security information,and the specific definition of security policies.The specifications about compatibility of terminals specially need to be written into widely recognized 3GPP/3GPP2 standards because they require the support of handset manufacturers in the world.Besides,the complexity of the A-IMSsecurity system increases the difficulty of system implementation.For example,the faulty system design will affect the system's stability,thus hindering the popularization of its application.Nevertheless,the A-IMShas advanced security concepts,which can meet the practical demands of operators.Therefore,it will probably become the security standard for the next-generation converged network.

