Guidance laws for attacking defended target
Qilong SUN, Chenfeng ZHANG, Ning LIU, Weixue ZHOU, Niming QI
a Beijing Institute of Space Long March Vehicle, Beijing 100076, China
b Department of Aerospace Engineering, Harbin Institute of Technology, Harbin 150001, China
KEYWORDS
Attacking;
Control effort;
Differential game theory;
Guidance law;
Miss distance
Abstract In this paper,two new guidance laws based on differential game theory are proposed and investigated for the attacker in an attacker-defender-target scenario.The conditions for the attacker winning the game are analyzed when the target and defender using the differential game guidance law based on the linear model. The core ideas underlying the two guidance laws are the attacker evading to a critical safe boundary from the defender,and then maintaining a critical miss distance.The guidance law more appropriate for the attacker to win the game differs according to the initial parameters. Unlike other guidance laws, when using the derived guidance laws there is no need to know the target and the defender’s control efforts. The results of numerical simulations show that the attacker can evade the defender and hit the target successfully by using the proposed derived guidance laws.
1. Introduction
When a missile (attacker) intercepts an aircraft (target), the aircraft will launch a defense missile (defender) to protect itself, making it difficult for the attacker to hit the aircraft.Thus, guidance laws that enable the attacker to overcome this difficulty in such engagements is desired.
The traditional attack-defense scenario consists of two players:an attacking missile and an evasive target.1-3Recently various pursuit-evasion scenarios involving multiple agents have been developed.Separate scenarios involving two players against one target were presented by Liu et al.4and Ganebny et al.5In those scenarios,two players worked to minimize the miss distance, whereas the target endeavored to maximize it.Refs.6,7investigated a scenario in which multiple missiles pursued one target. Active defense scenarios in which a ship launched a defender against an incoming attacker were also presented.8-10Rusnak11investigated a three-player conflict in which a woman endeavored to evade a bandit and her bodyguard tried to intercept the bandit before the bandit caught her. The problem was analyzed using the differential games theory and multi-objective optimization.In recent years,interest has been increasing in the aircraft active defense scenario.Two similar cooperative guidance laws aimed at protecting the aircraft had been proposed.12,13In these proposed laws,the target and the defender had information about the attacker and the core idea was to control the defender such that it always remained in the attacker-target’s line-of-sight. Numerical simulations had shown that a defender that used the derived cooperative line-of-sight guidance law fared better than a defender that only used the proportional navigation guidance law. Shima14presented a scenario in which the guidance law of the attacker was a linear form that was known to the defender and the target.The defender and the target cooperated with each other to guarantee that the defender could intercept the attacker before it hit the target. Shaferman and Shima15proposed a multiple model adaptive control scheme that estimated a possible homing missile guidance law in which the target and the defender were cooperative.Garcia et al.16-18analyzed the guidance law by using the nonlinear method. In Ref.17, they investigated the cooperative defended guidance law with the defender and the target working against the attacker using differential game theory. Kumar and Shima19derived a cooperative nonlinear guidance law based on the sliding model control theory under the assumption that the guidance law of the attacker was linear. Perelman et al.20derived a cooperative differential game guidance law based on a linear model. Further, a scenario in which two defenders protected the target was investigated.21In this paper the cooperative guidance law was one-way.
Ratnoo and Shima22analyzed the conditions for the attacker to evade the defender and hit the target when the defender and attacker used different guidance laws.In the scenario,the attacker ignored the defender and only used its guidance law to hit the target. A guidance law (Evade to a Boundary and Pursuit Guidance Law (EBPGL)) for the attacker to evade the defender and intercept the target was also investigated based on differential game theory by Rubinsky and Gutman.23In their study,the target used its optimal evasion strategy to evade the attacker and the defender used its optimal pursuit strategy to pursue the attacker. Further, the defender and the target were independent and they did not help each other. The core idea of the attacker was to evade to the safe boundary and then change the guidance law to the optimal pursuit strategy.For the attacker to win the game,the attacker needed to know the control effort information(maximum acceleration) of the target and the defender. However,obtaining such information was difficult.An evasion and pursuit guidance law was also presented based on differential game theory.24,25In Ref.24,the attacker chose an appropriate acceleration to evade the defender and then pursued the target.The attacker also needed to know the control effort of the rivals. Weiss et al.26,27proposed a method that guaranteed the required maximum miss distance for pursuit and the required minimum miss distance for evasion by using minimum effort assuming that the information was perfect.
In the past works, the guidance law in the active defense scenario always focused on the cooperative guidance law between the target and the defender to intercept the attacker.The guidance law for attacking the defended target is scarce,and it is always analyzed under the assumption that control efforts of the players are bounded and the velocities of the players are fixed in the engagement.Meanwhile,the velocities,positions,and control efforts of the defender and the target are known to the attacker.23-26The strategy presented by Rubinsky and Gutman23is unsuited for the condition that the Zero-Effort-Miss (ZEM) distance between the attacker and the target is large, and the ZEM distance between the attacker and the defender is small. The guidance law needs to know the strategies of the defender and the target,24-26however, the control effort is difficult to obtain accurately. In this paper,we also assume that the control efforts of the players in the active defense scenario are bounded and that the velocities and positions of the defender and target are known to the attacker. However, the control effort information is unknown to the attacker. Under these assumptions, two new guidance laws are designed for the attacker to win the game under different conditions based on differential game theory. In this paper,the ZEM distance is used as the index.In past research,the attacker always evades to a safe miss distance boundary that is the same sign as the initial ZEM distance. However,in some circumstances,the attacker evading to a safe miss distance boundary that has an opposite sign as the initial ZEM distance will be better.The presented guidance laws are suited not only for the scenario that presented by Rubinsky and Gutman23, but also for the condition that the ZEM distance between the attacker and the target is large,and the ZEM distance between the attacker and the defender is small.
2. Problem formulation
2.1. Nonlinear model

The closing speeds VATand VADbetween the entities are
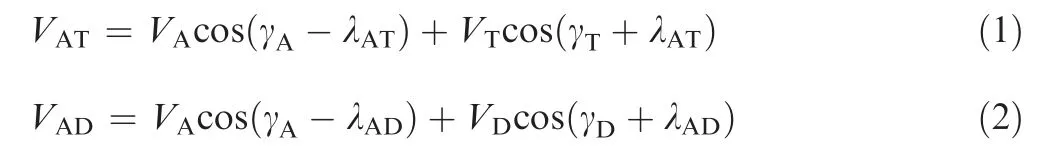
The rates of the angles of the line-of-sight are
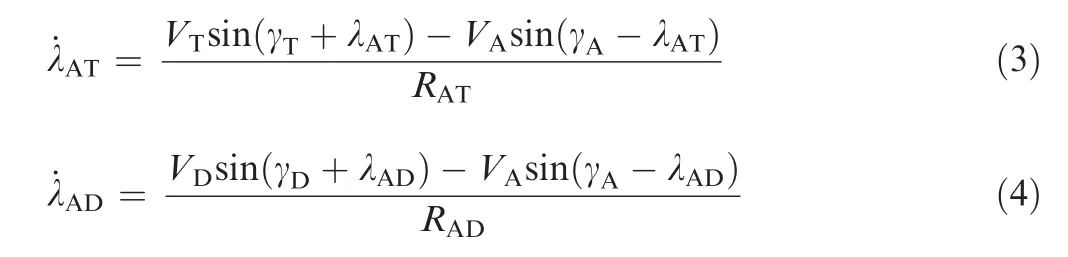
It is assumed that the dynamics of each agent can be represented by linear equations:
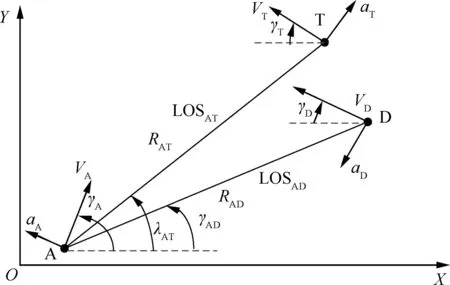
Fig. 1 Illustration of engagement involving attacker (A), target(T), and defender (D).
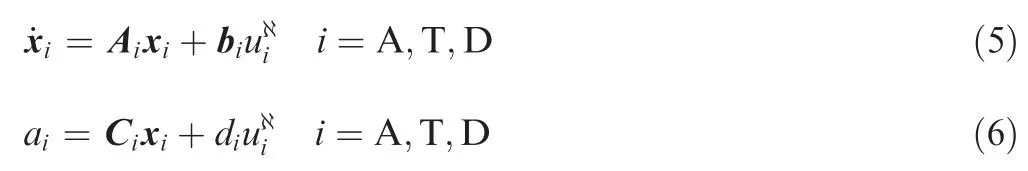
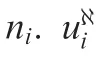
The rates of the flight path angles are

2.2. Linearized kinematics
It is assumed that the engagements take place near the collision triangles, thus,we can linearize the problem around the initial line-of-sight. LOSAT0and LOSAD0represent the initial line-ofsight between the attacker and target,and between the attacker and defender, respectively. yATand yADare the relative displacement between the attacker and the target normal to LOSAT0, and the relative displacement between the attacker and the defender normal to LOSAD0, respectively. In order to linearize the problem around the initial line-of sight,we denote uALand uTLas the accelerations of the attacker and the target perpendicular to LOSAT0, respectively; uDLis denoted as the acceleration of the defender perpendicular to LOSAD0. For the sake of simplicity,it is assumed that the attacker,the target and the defender obey ideal dynamics; thus,Ai=0,bi=0,Ci=0,di=1, and uiL(i=A, T, D) are
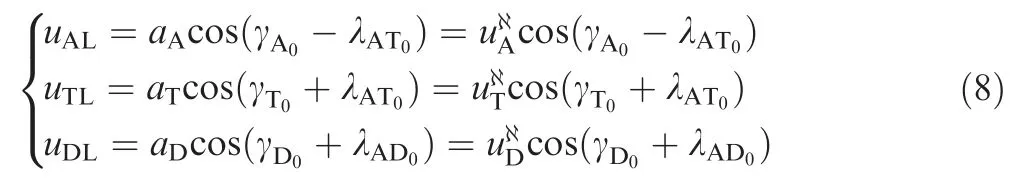
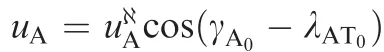
The state vectors of the engagement are
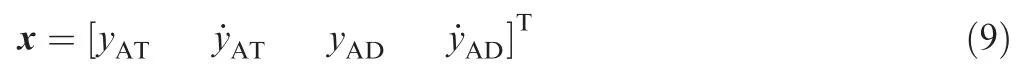
The equations of motion are
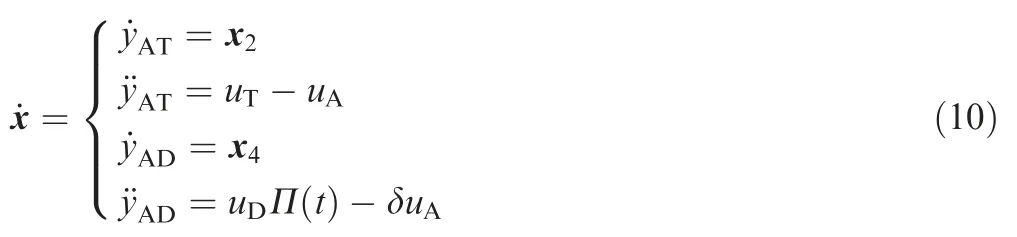
where δ=cos(γA0-λAD0)/cos(γA0-λAT0). It is assumed that the defender is launched from the target, δ is a positive value.Π(t) is an indicator function reflecting the state of the defender, and it is

The equations of motion can be rewritten as
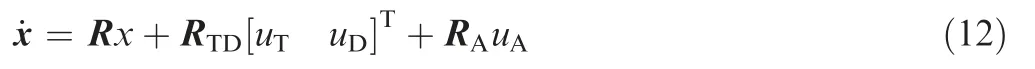
where
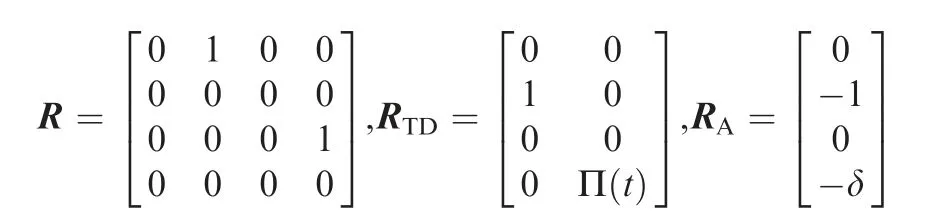

where RAT0and RAD0are the initial ranges between the attacker and the defender,and between the attacker and defender, respectively. VAT0and VAD0are the initial closing speeds,and they are
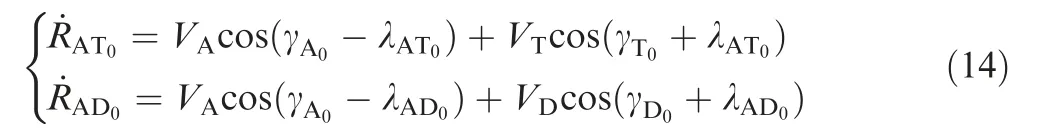
The time-to-go of the engagements are

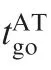
3. Differential game between entities
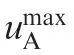
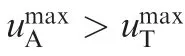
3.1. Order reduction
The ZEM distances between the attacker and the target, and between the attacker and defender are denoted as ZAT(t) and ZAD(t), respectively. ZATt( ) and ZAD(t) can be obtained using

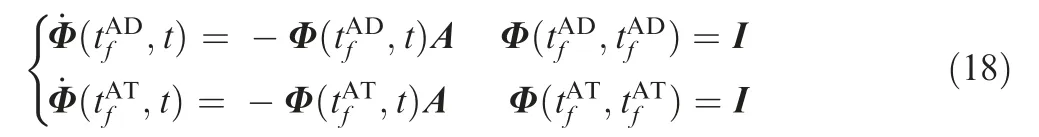
and ηATand ηADare

Combining Eqs. (16)-(19), then substituting gives
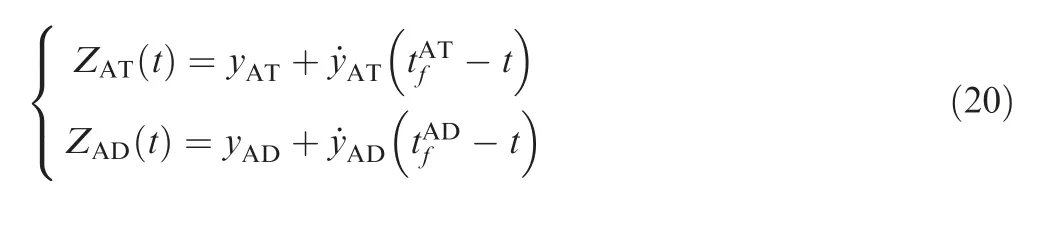
3.2. Differential game guidance laws
The dynamics of ZAT(t) and ZATt( ) are given by
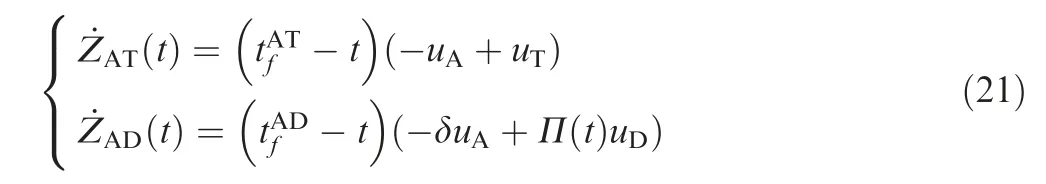
In the attacker-target engagement,the aim of the attacker is to minimize the miss distance;conversely,the aim of the target is to maximize the miss distance.The cost function to solve the problem is

As yAT, the cost function can be rewritten as follows:

The optimal strategy of the attacker is to minimize the cost function, whereas that of the target is to maximize the cost function. The optimal strategies for the two players in this game can be easily obtained, and the optimal guidance laws are

In the attacker-defender engagement, the aim of the attacker is to maximize the miss distance, whereas that of the defender is to minimize the miss distance. Similarly, the cost function to solve the problem is

The optimal strategy of the attacker is to minimize the cost function, whereas that of the defender is to maximize the cost function. Both players’ optimal strategies can be easily obtained.
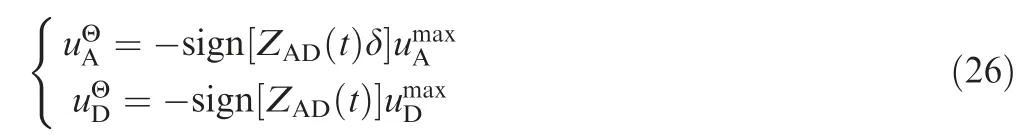
Because δ is a positive value, Eq. (26) can be written as follows

In order for the attacker to win the game,we need to design a feasible guidance law that guarantees that the attacker evades the defender and successfully attains the target. Two cases are discussed.
Case 1. the signs of ZATt=0( ) and ZADt=0( ) are opposite.
For this case,it is known that-sign ZADt( )[ ]=sign ZATt( )[ ].The optimal strategies of the attacker in Eqs.(24)and(26)are the same. If the attacker uses the optimal evasion strategy to evade the defender, it can also successfully pursue the target.The time evolutions of the ZEM distances for this case are shown in Fig. 2. In the figure, the ZEM distance between the attacker and the target is shown as ZAT(t), that between the attacker and the defender is shown as ZAD. Similarly, In the subsequent figures,the time evolutions of the ZEMs are shown as ZAT(t) and ZAD(t).
In Fig. 2, ZAT(t=0) and ZAD(t=0) satisfy
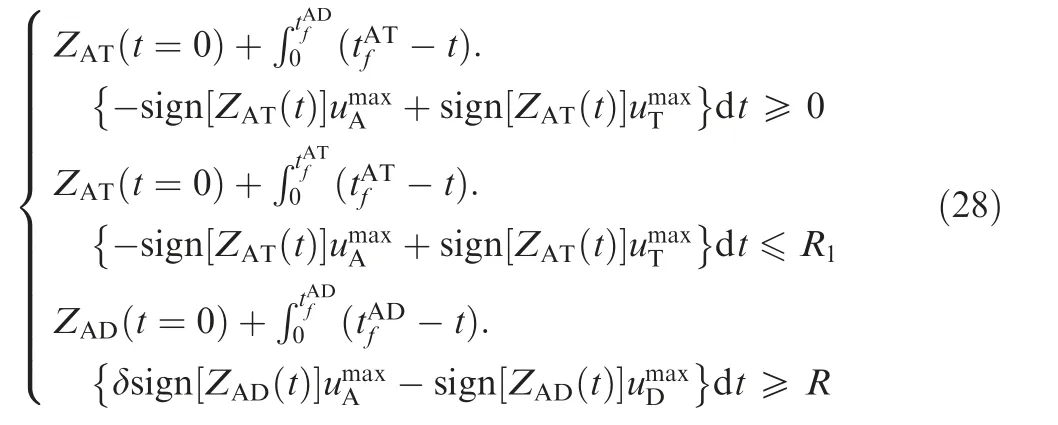
where R is the kill radius of the defender;thus,if the miss distance between the attacker and the defender is not greater than R, the attacker will be intercepted. R1is the kill radius of the attacker; thus, if the miss distance between the attacker and the target is not greater than R1, the attacker will win the game.
Thus, the ranges are
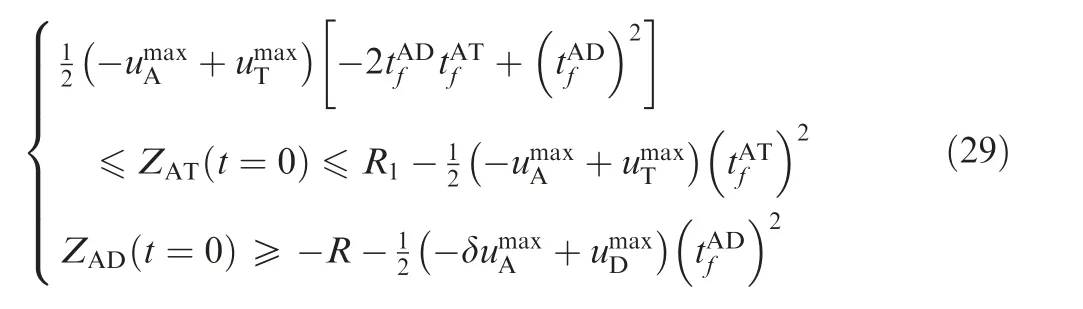
This case is simple, as the attacker only needs to use the optimal pursuit strategy to accomplish the evasion and pursuit task.
Case 2. the signs of ZATt=0( ) and ZADt=0( ) are the same.
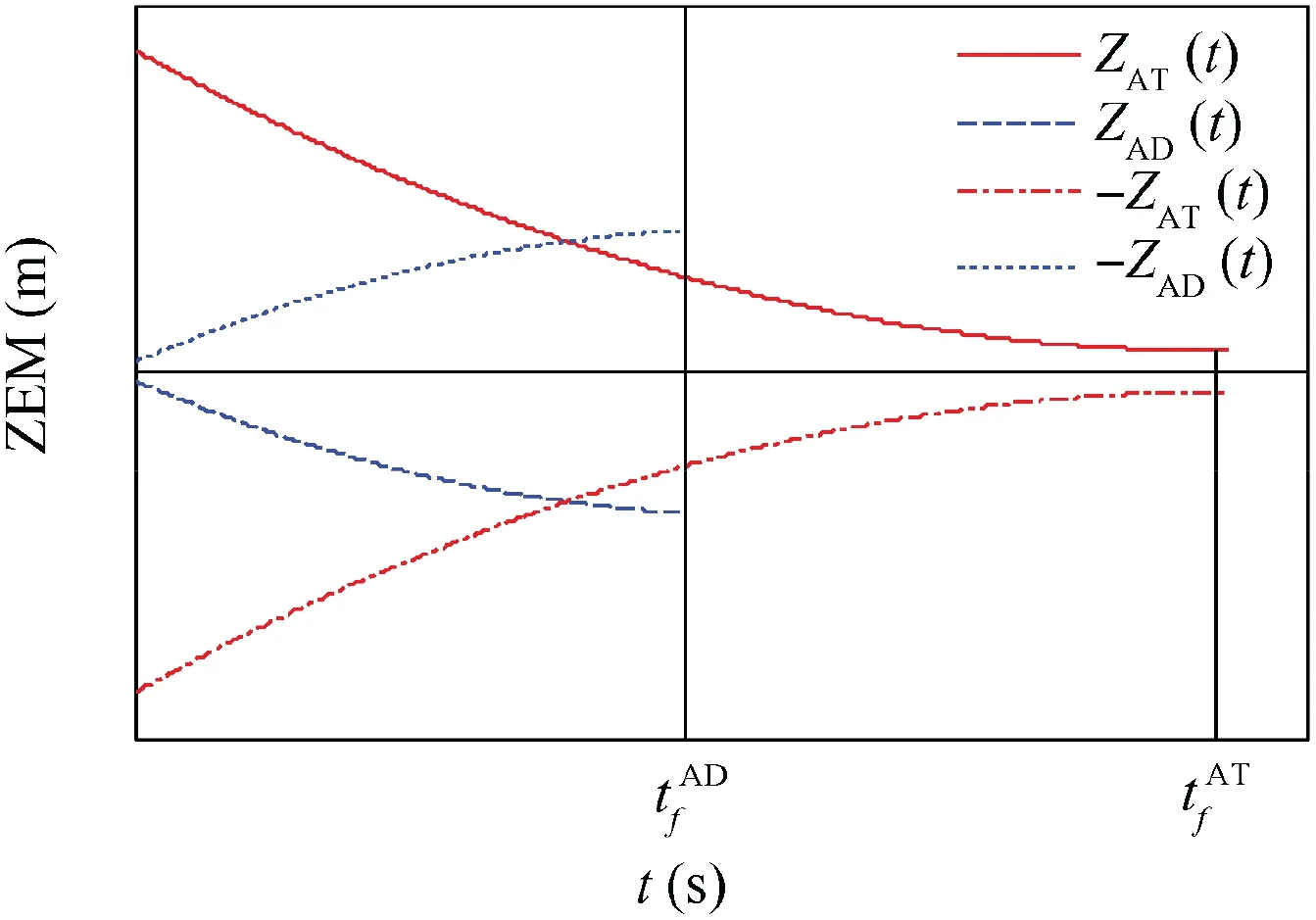
Fig. 2 Time evolutions of ZEMs distances.
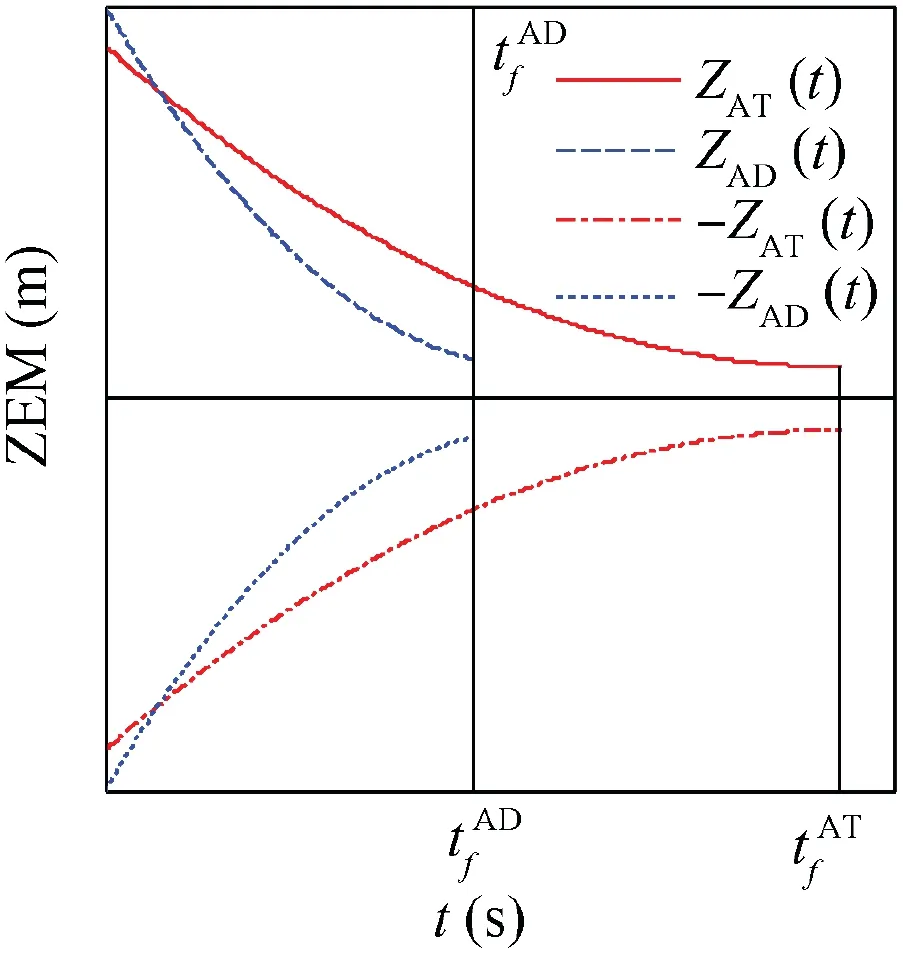
Fig. 3 Attacker ZEMs for optimal pursuit strategy.
For this case, we need to design a reasonable guidance law for the attacker to accomplish the evasion and pursuit task.
3.3. Design of attacker’s guidance law
In consideration of the attacker easily being intercepted by the defender,the attacker uses the OPGL under the condition that the signs of ZATt=0( ) and ZADt=0( ) are the same. Meanwhile, if the attacker uses the EPGL, it cannot pursue the target because of the large ZATt( ). Thus, we design a new guidance law for the attacker. The cost function is
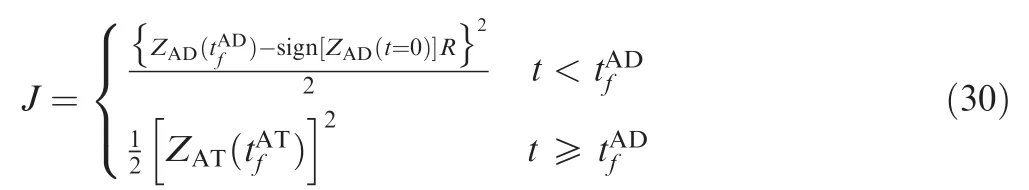

The adjoint equation and transversality condition are as follows:
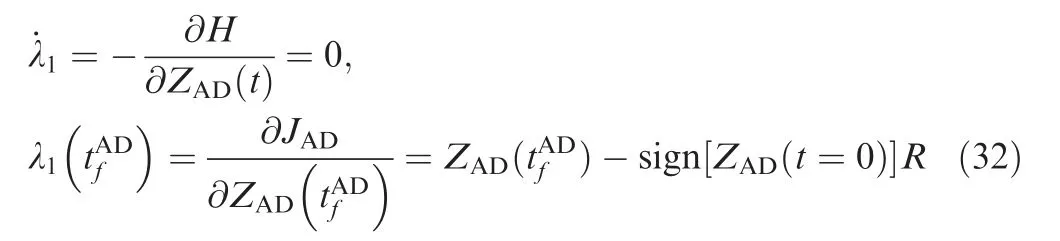
Thus, λ1can be obtained using
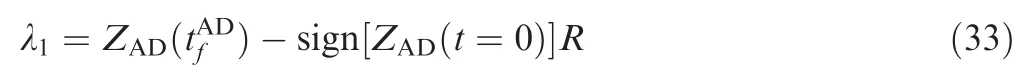
Substituting Eq. (33) into Eq. (31), we obtain
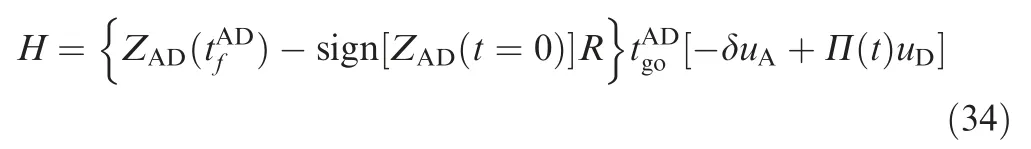
The attacker tries to minimize H,whereas the defender tries to minimize the miss distance from the attacker. Thus, the optimal strategy of the defender is given by Eq. (26). Meanwhile, the optimal strategy of the target is given by Eq. (24).We can solve the close-loop optimal strategy of the attacker using
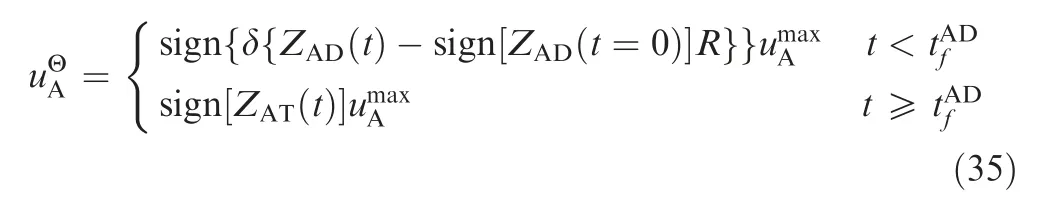
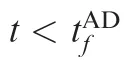
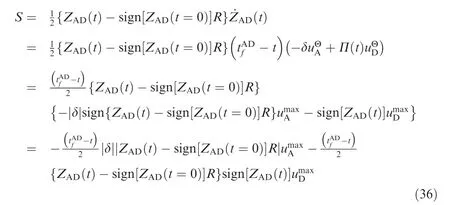
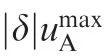
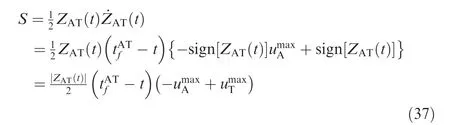
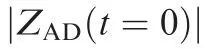
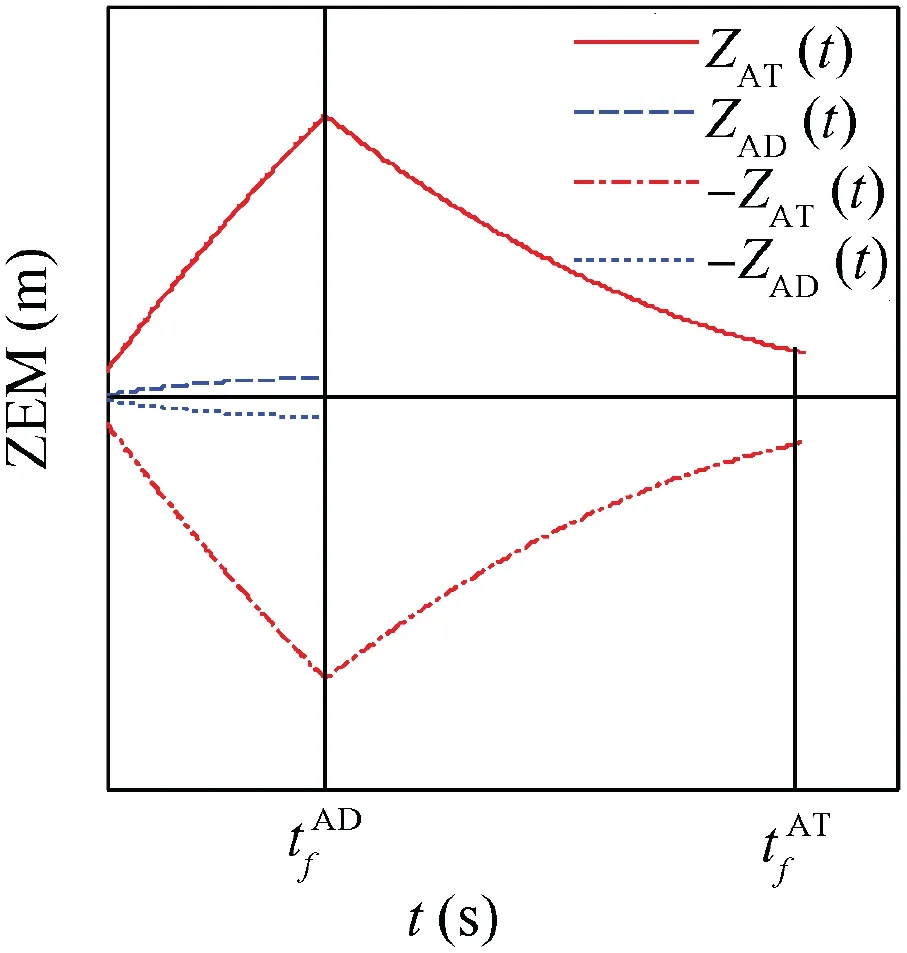
Fig. 4 Attacker ZEMs for optimal evasion-pursuit strategies.
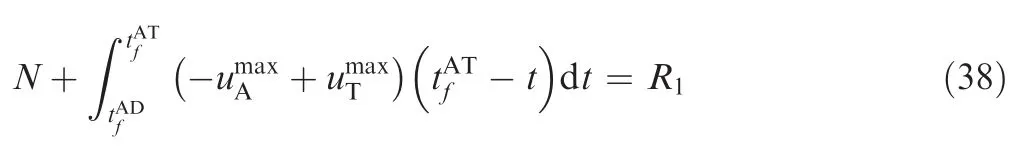
N can be given by
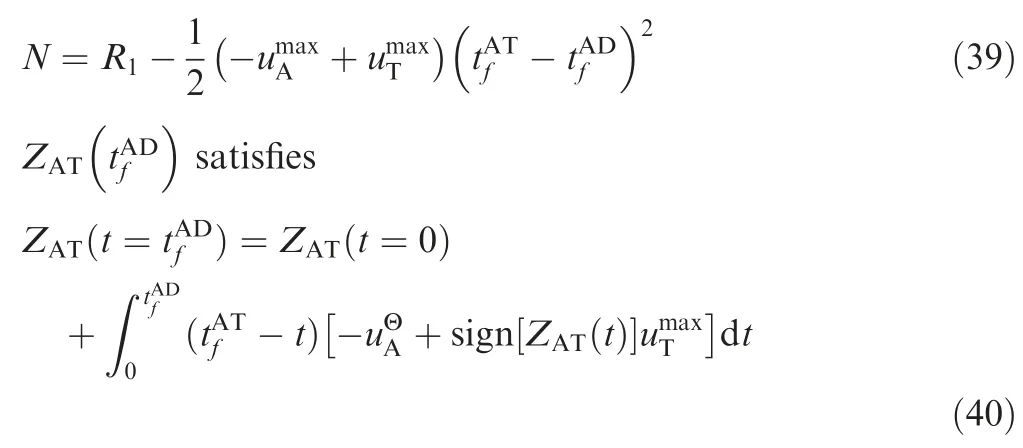
Thus, SSBGL needs to satisfy
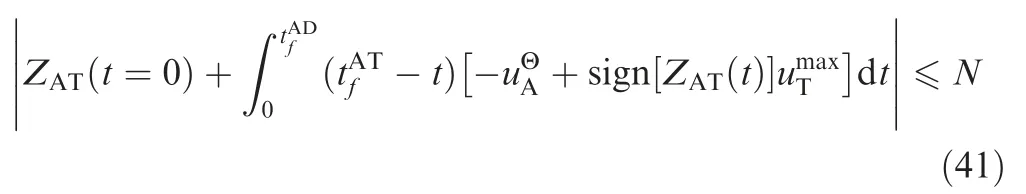
Substituting Eq. (35) into Eq. (41), we obtain
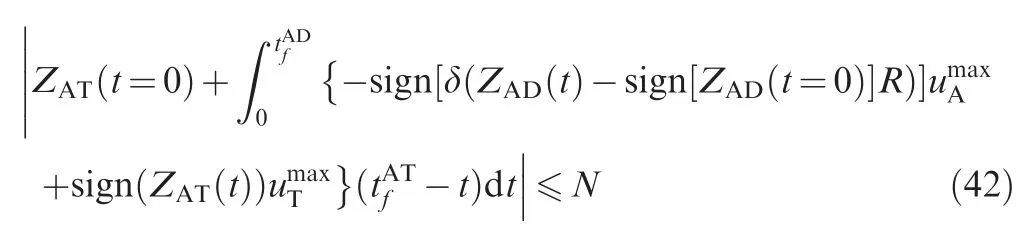
We solve for the analytical solutions for three general cases.
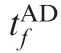
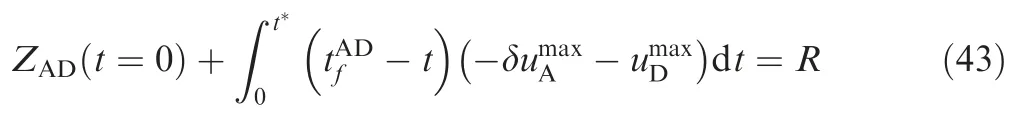
t*can be given by
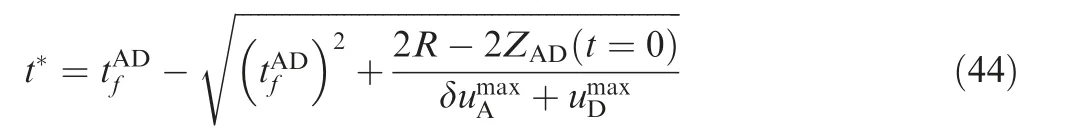
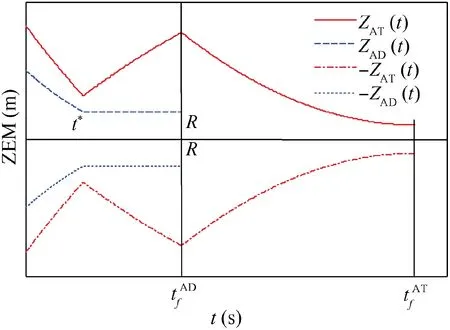
Fig. 5 Time evolutions of ZEMs in Case 1 by using SSBGL.
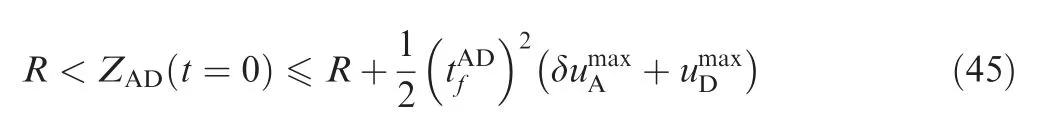
In Fig. 5, ZAT(t=0) is a relatively large value, and ZAT(t=0) needs to satisfy
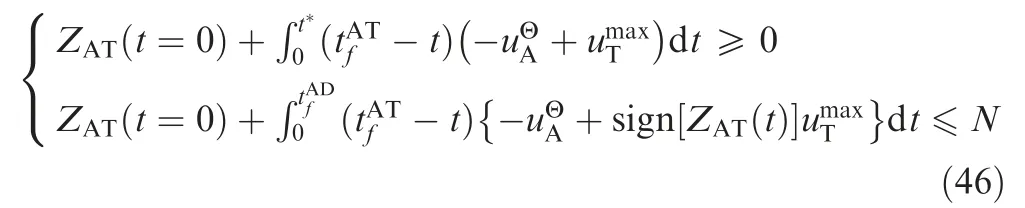
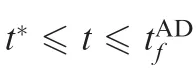
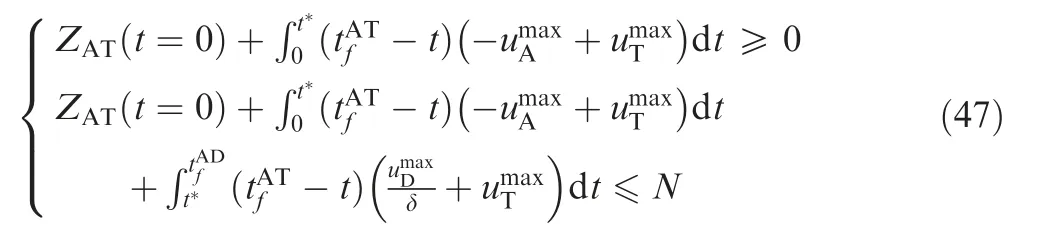
Substituting Eqs. (44) and (39) into Eq. (47), we obtain

where
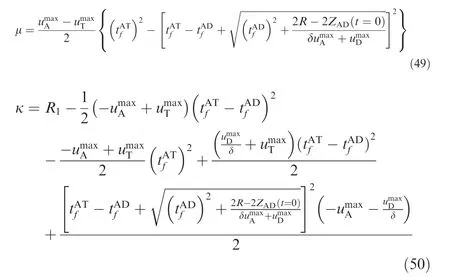
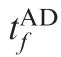
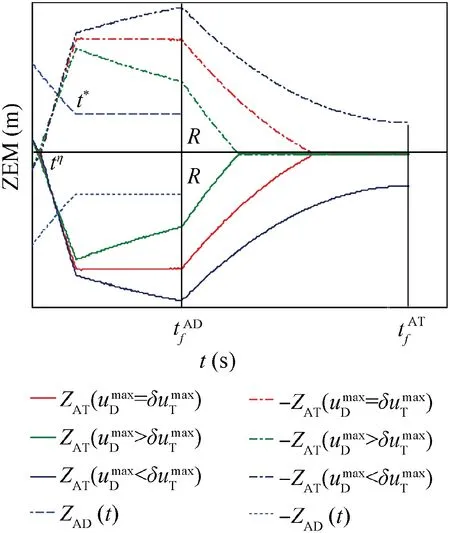
Fig. 6 Time evolutions of ZEMs in Case 2 by using SSBGL.
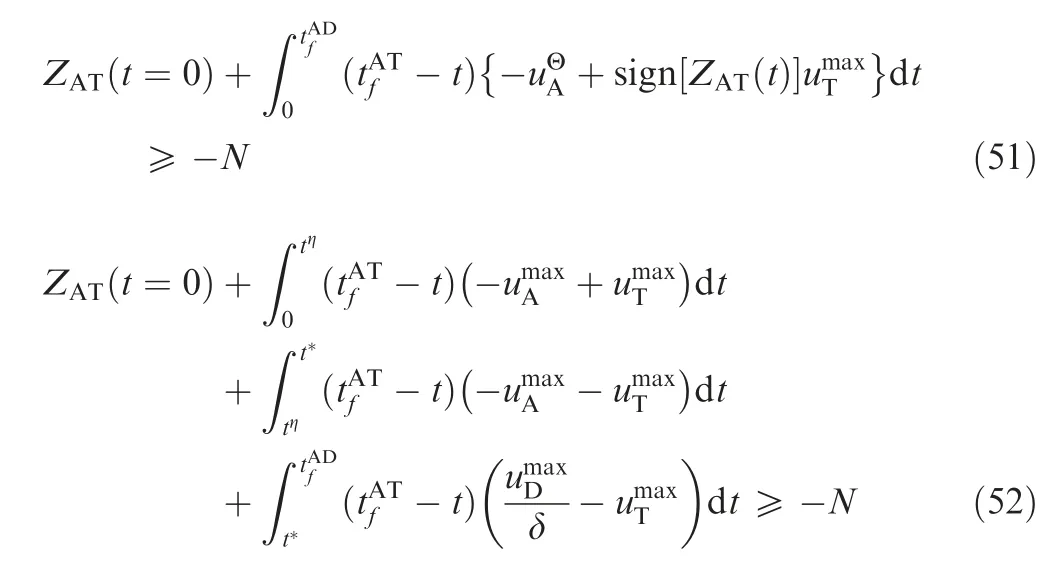
tηsatisfies ZAT(tη)=0; thus,
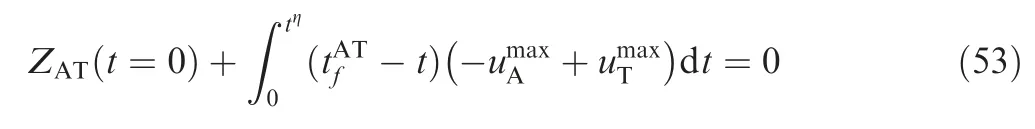
tηcan be given by
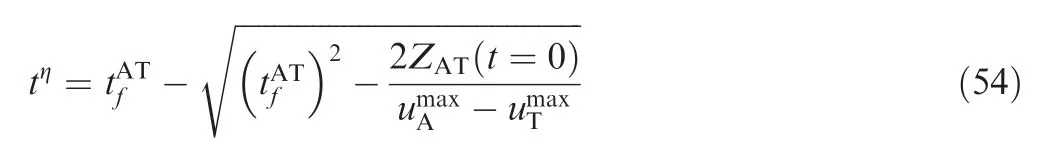
In Fig. 6, it satisfies

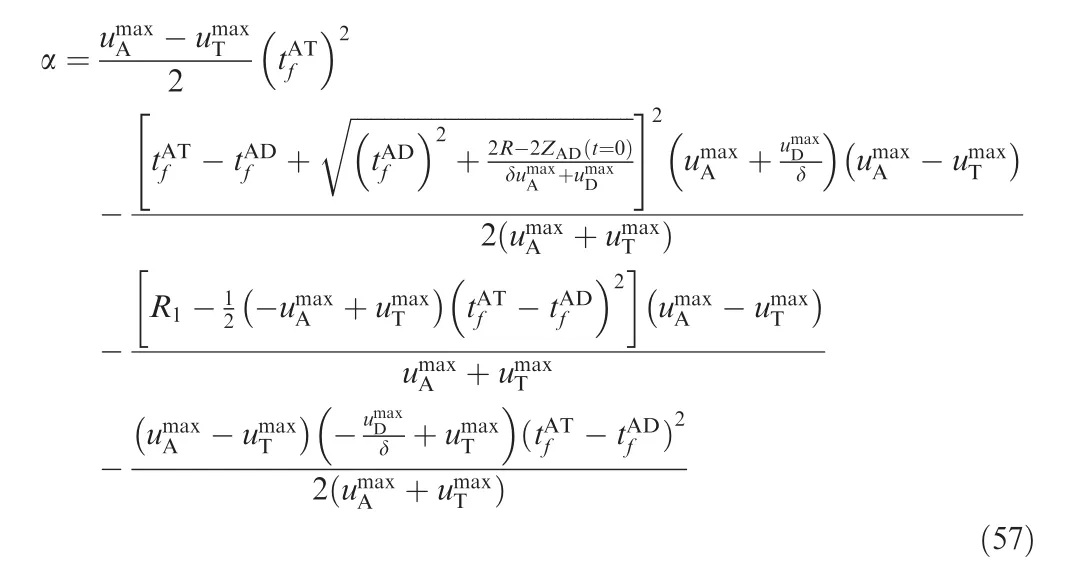
Thus, substituting Eq. (39) into Eq. (52), and combining Eq. (55), we obtain

where
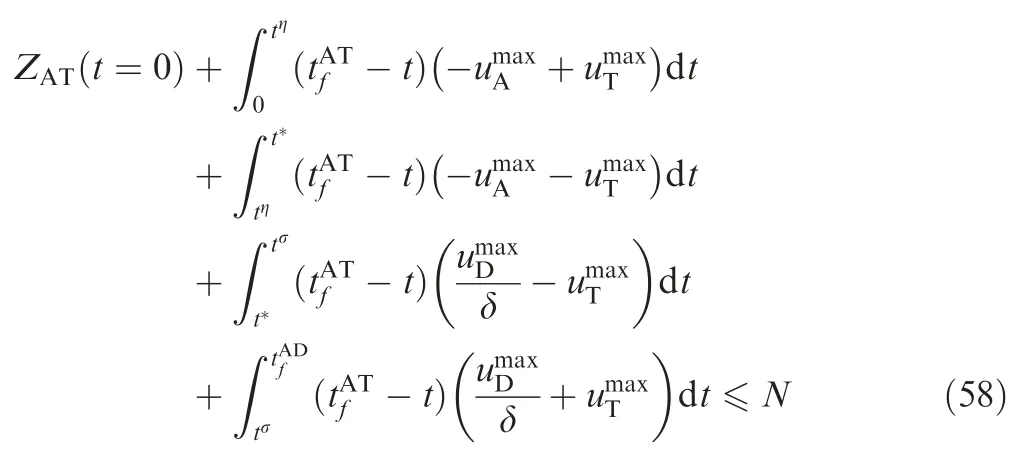
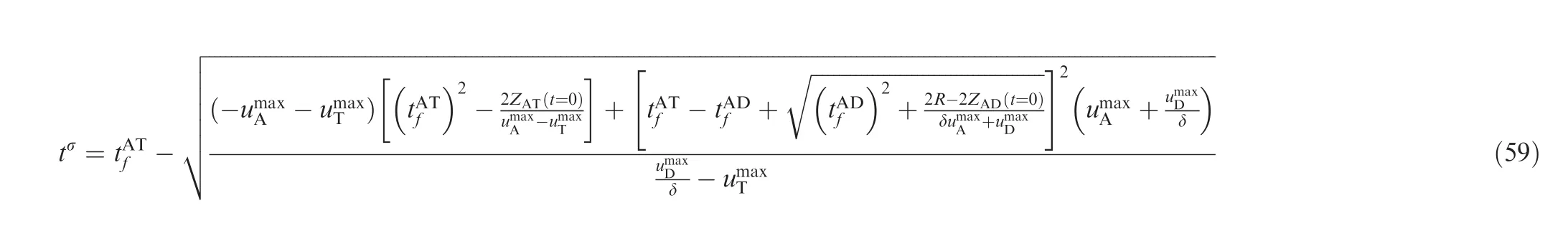
where ZAT(tσ)=0. tσsatisfies
Thus, in Fig. 7, ZAT(t=0) satisfies

where
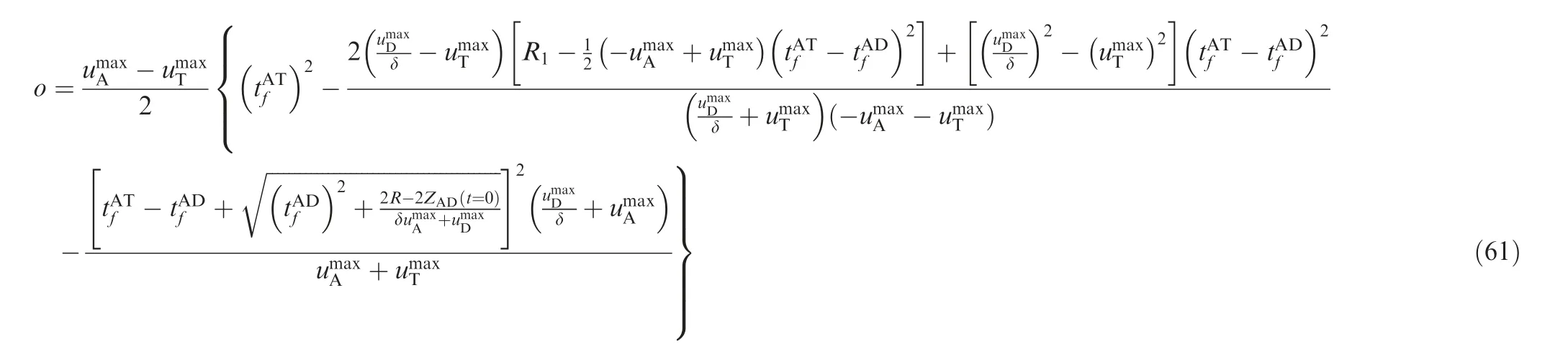
(1) If the range α ≤ZAT(t=0)<μ exists, then ZAT(t =0)=α is the low boundary value for the attacker to win the game using SSBGL.
(2) If the range μ ≤ZAT(t =0)≤κ exists, then ZAT(t =0)=κ is the upper boundary value for the attacker to win the game using SSBGL.
(3) If the range 0 ≤ZAT(t=0)<o exists, then ZAT(t =0)=o is the upper boundary value for the attacker to win the game using SSBGL.
(2) and (3) cannot occur at the same time.
Theorem 1. If (1) and (2) hold true, the attacker can win the game by using SSBGL when ZAT(t=0)∈α,κ[ ].
Theorem 2. If (1) and (3) hold true, the attacker can win the game by using SSBGL when ZAT(t=0)∈α,o[ ].
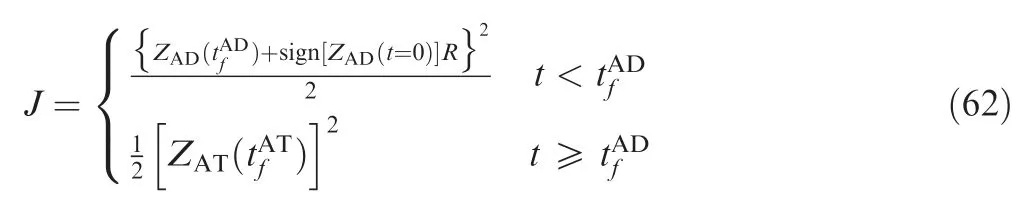
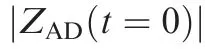
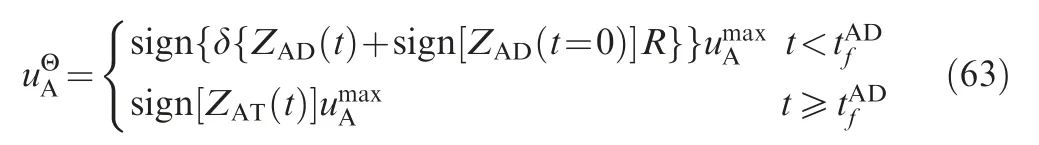
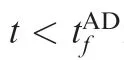
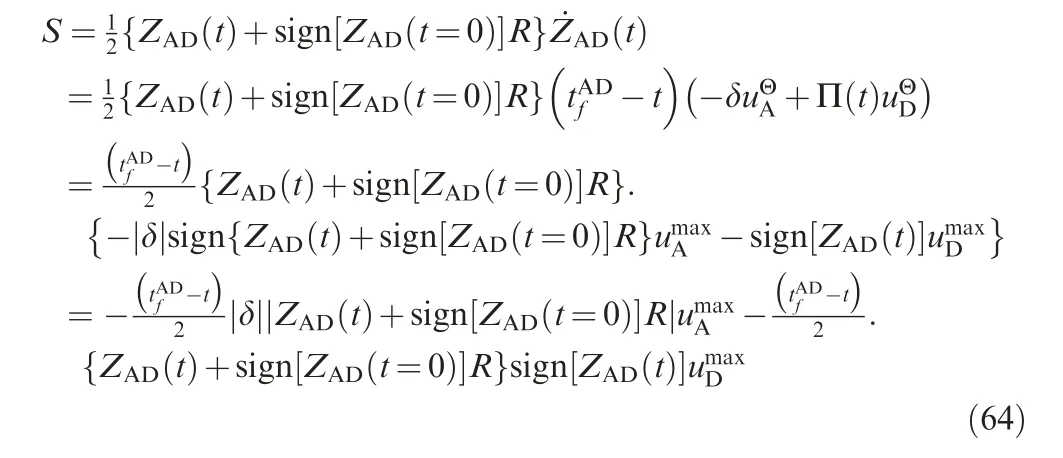
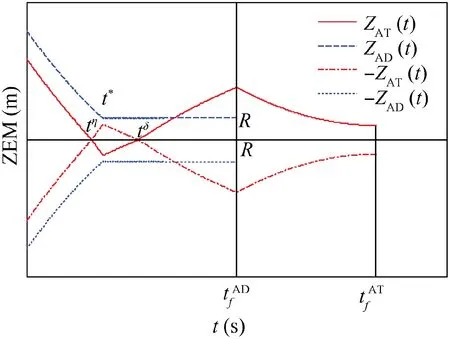
Fig. 7 Time evolutions of ZEMs in Case 3 by using SSBGL.
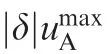
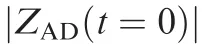
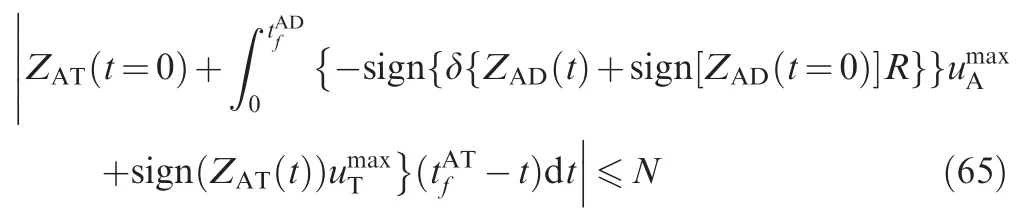
We solve the analytical solutions for three general cases:
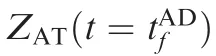
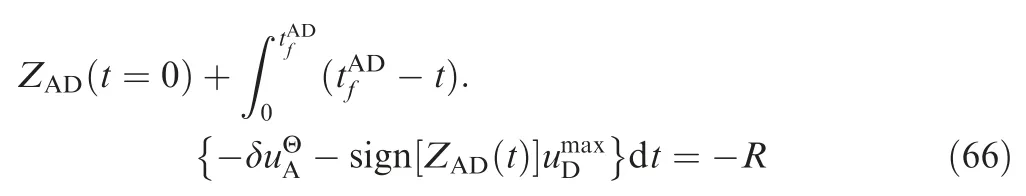
In Fig. 8 tχsatisfies ZAD(tχ)=0, thus, we obtain
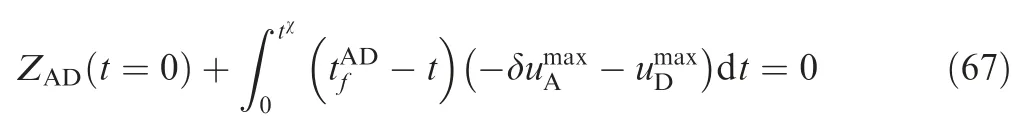
tχcan be given by
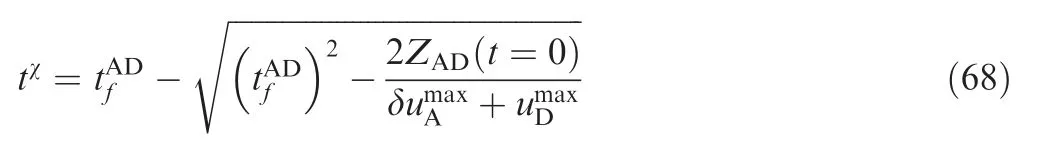
tεsatisfies ZAD(tε)=-R; thus,
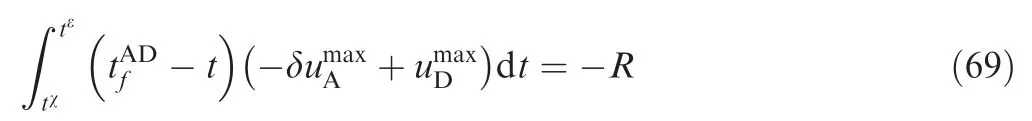
tεcan be given by
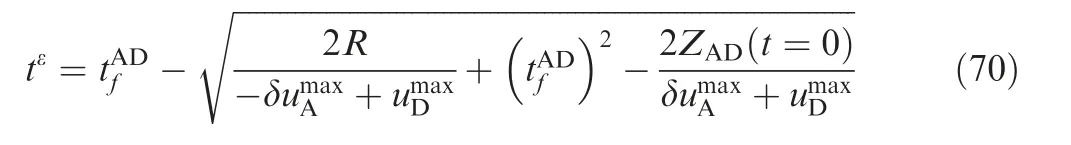
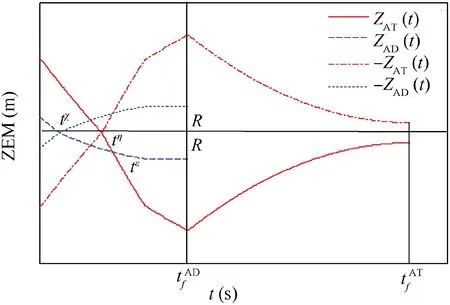
Fig. 8 Time evolutions of ZEMs in Case 1 by using OSBGL.
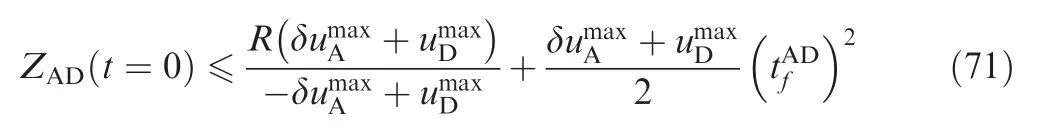
ZAT(t=0) satisfies
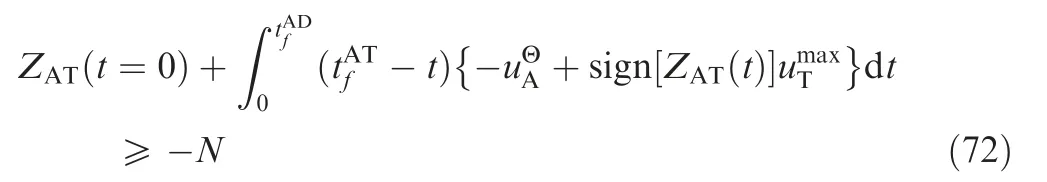
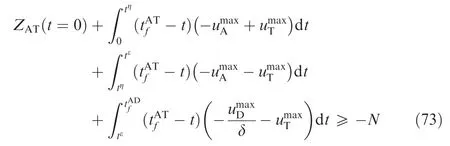
In Fig. 8, it satisfies

Thus, substituting Eq. (39) into Eq. (73), and combining Eq. (74), we obtain

where
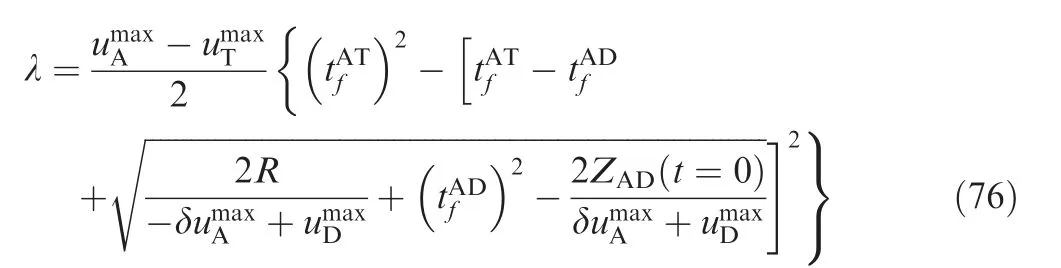
and
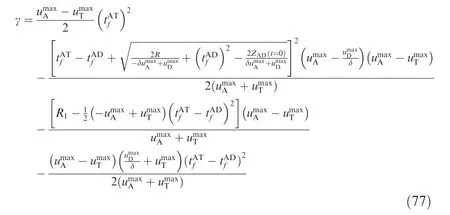
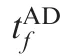
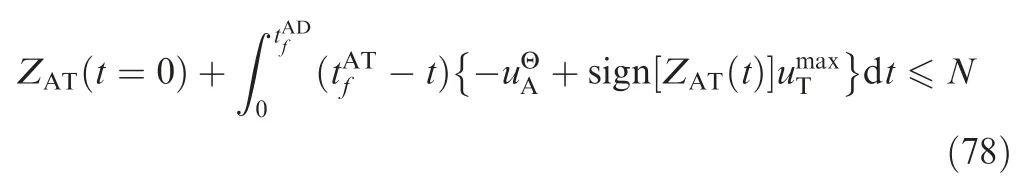
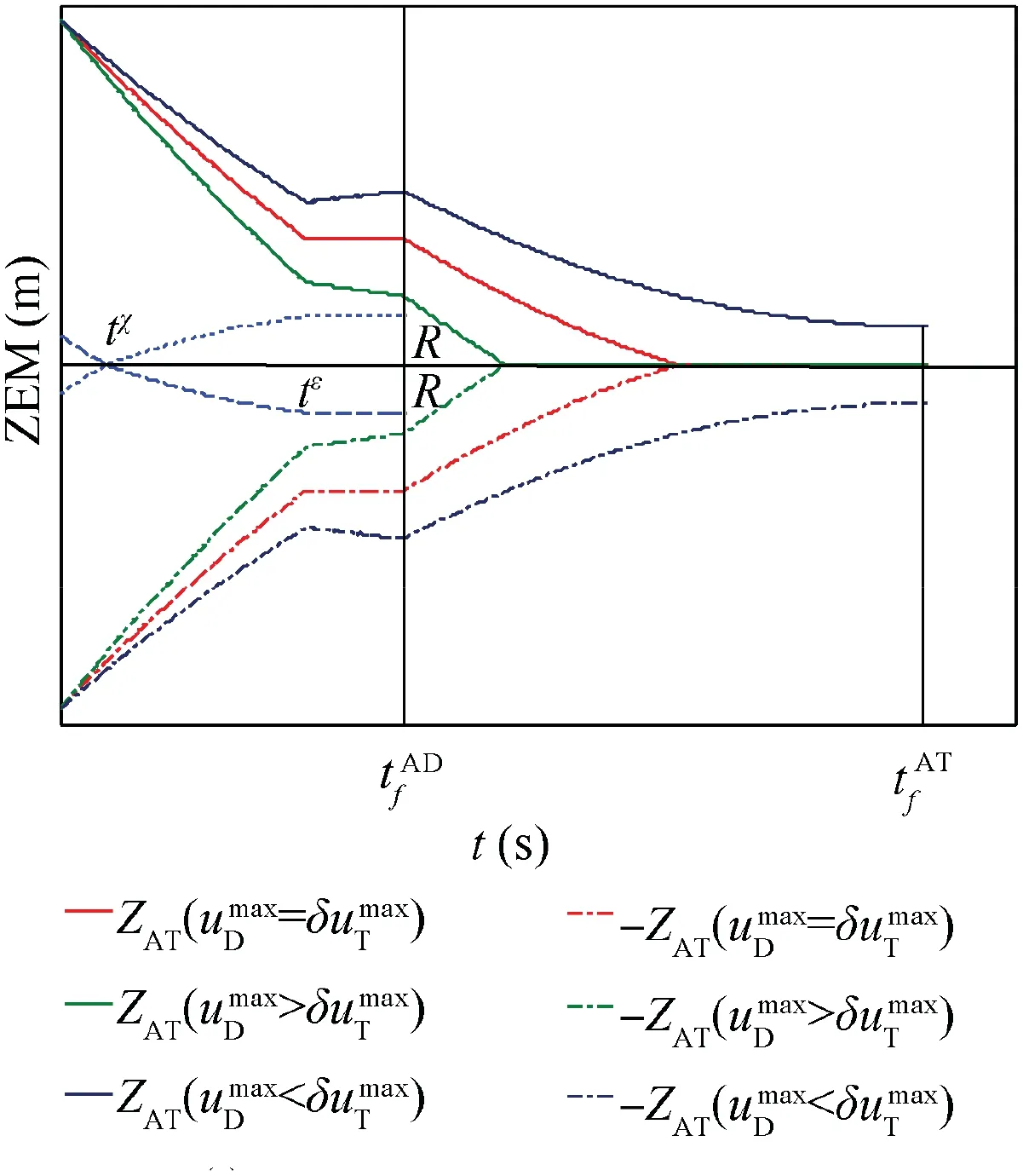
Fig. 9 Time evolutions of ZEMs in Case 2 by using OSBGL.
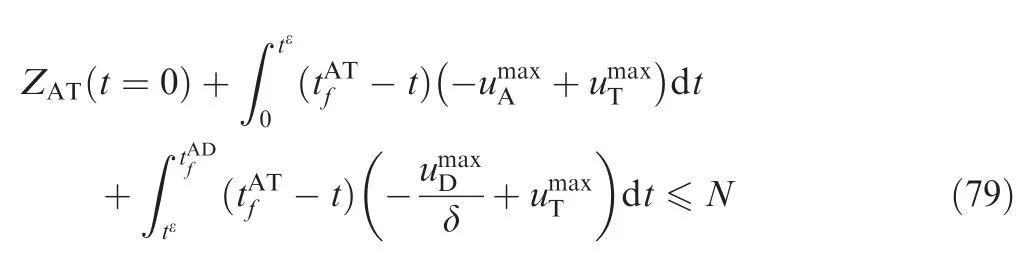
Combining Eqs. (79) and (88), ZAT(t=0) satisfies

where
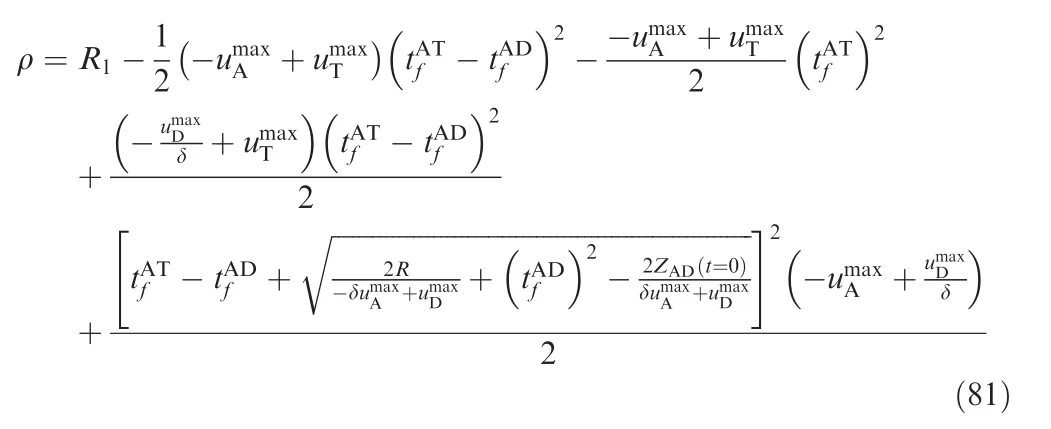
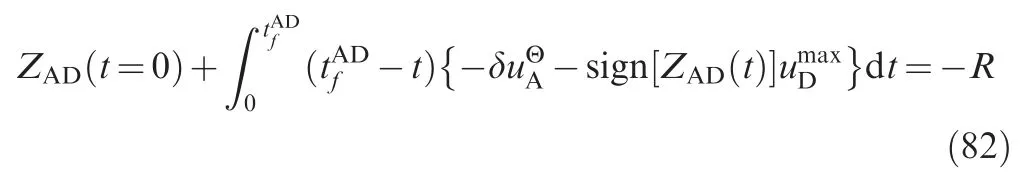
ZAT(t=0) satisfies
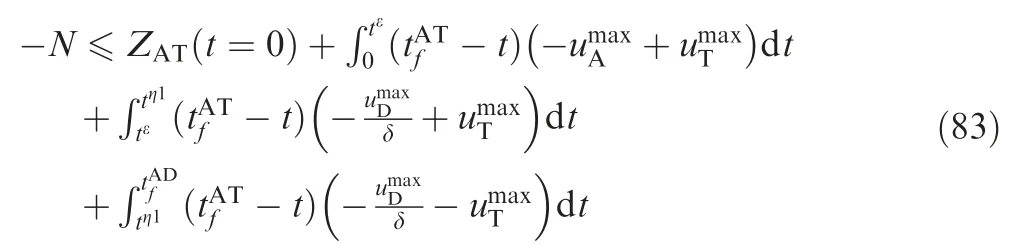
tη1satisfies ZAT(tη1)=0; thus,
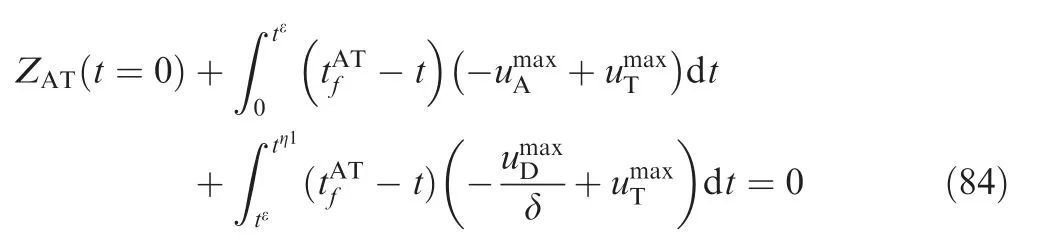
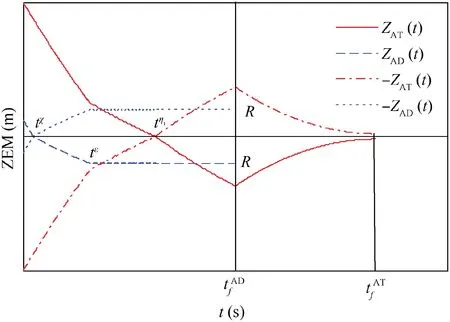
Fig. 10 Time evolutions of ZEMs in Case 3 by using OSBGL.
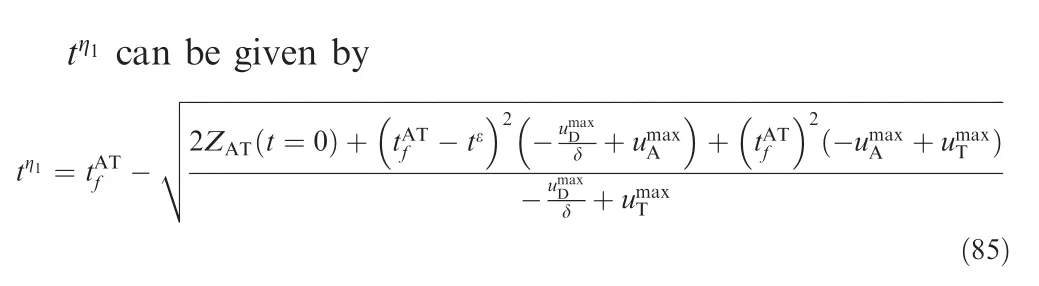
In Fig. 10, it satisfies

Combining Eqs (83) and (86), we obtain

where
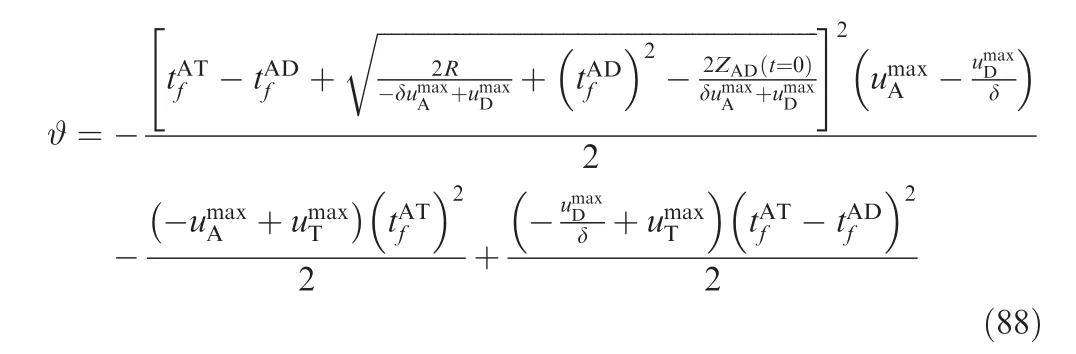
and
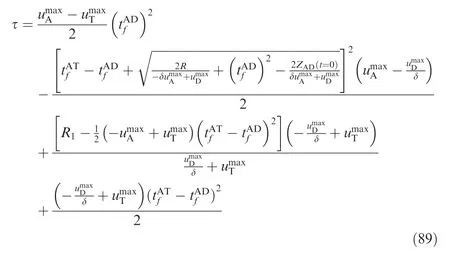
Thus, the following statements hold:
(1) If the range γ ≤ZAT(t =0)<λ exist, then ZAT(t =0)=γ is the low boundary value for the attacker to win the game using OSBGL.
(2) If the range τ ≤ZAT(t =0)<? exist, then ZAT(t =0)=τ is the low boundary value for the attacker to win the game using OSBGL.
(3) If the range ? <ZAT(t=0)≤ρ exist, then ZAT(t=0)=ρ is the upper boundary value for the attacker to win the game using OSBGL.
(1) and (2) cannot occur at the same time.
Theorem 3. If (1) and (3) hold true, the attacker can win the game using OSBGL when ZAT(t=0)∈γ,ρ[ ].
Theorem 4. If (2) and (3) hold true, the attacker can win the game using SSBGL when ZAT(t=0)∈τ,ρ[ ].
4. Nonlinear simulation
In this section,a nonlinear simulation that verifies the designed guidance law is presented. First, verification of the SSBGL is presented.
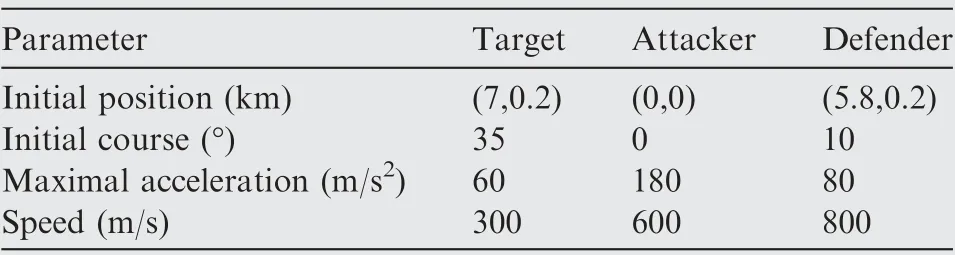
Table 1 Initial parameters for Case 1 by using SSBGL.
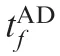
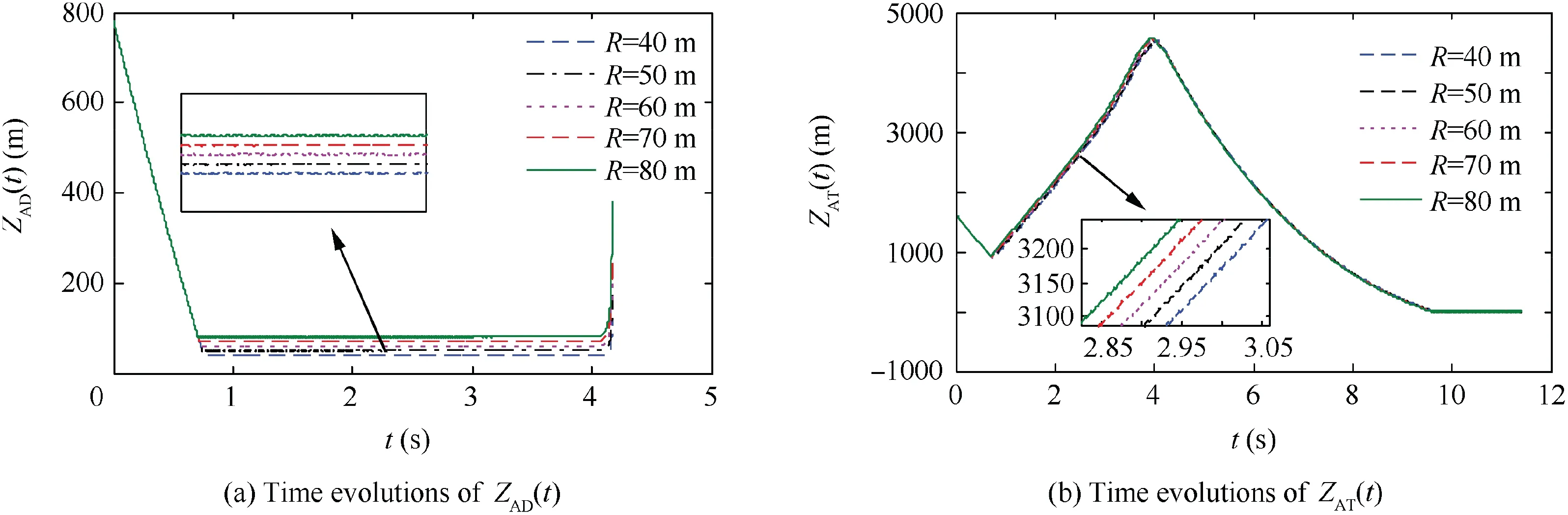
Fig. 11 Time evolutions of ZEMs in Case 1 by using SSBGL with various values of R.

Fig. 12 Trajectories in Case 1 by using SSBGL.
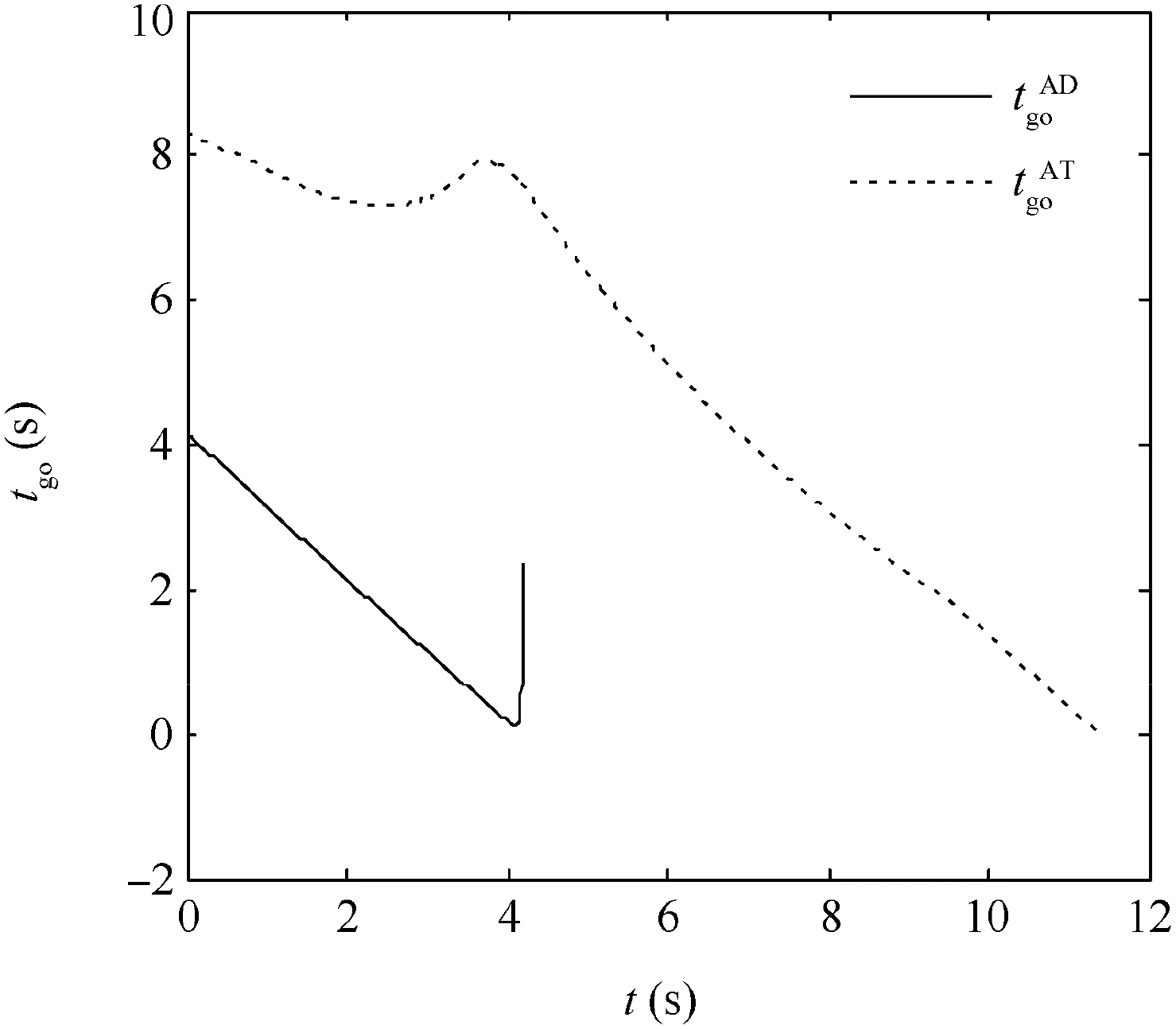
Fig. 13 Time-to-go in Case 1 by using SSBGL.
Table 2 Initial parameters for Case 2 by using SSBGL.
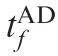
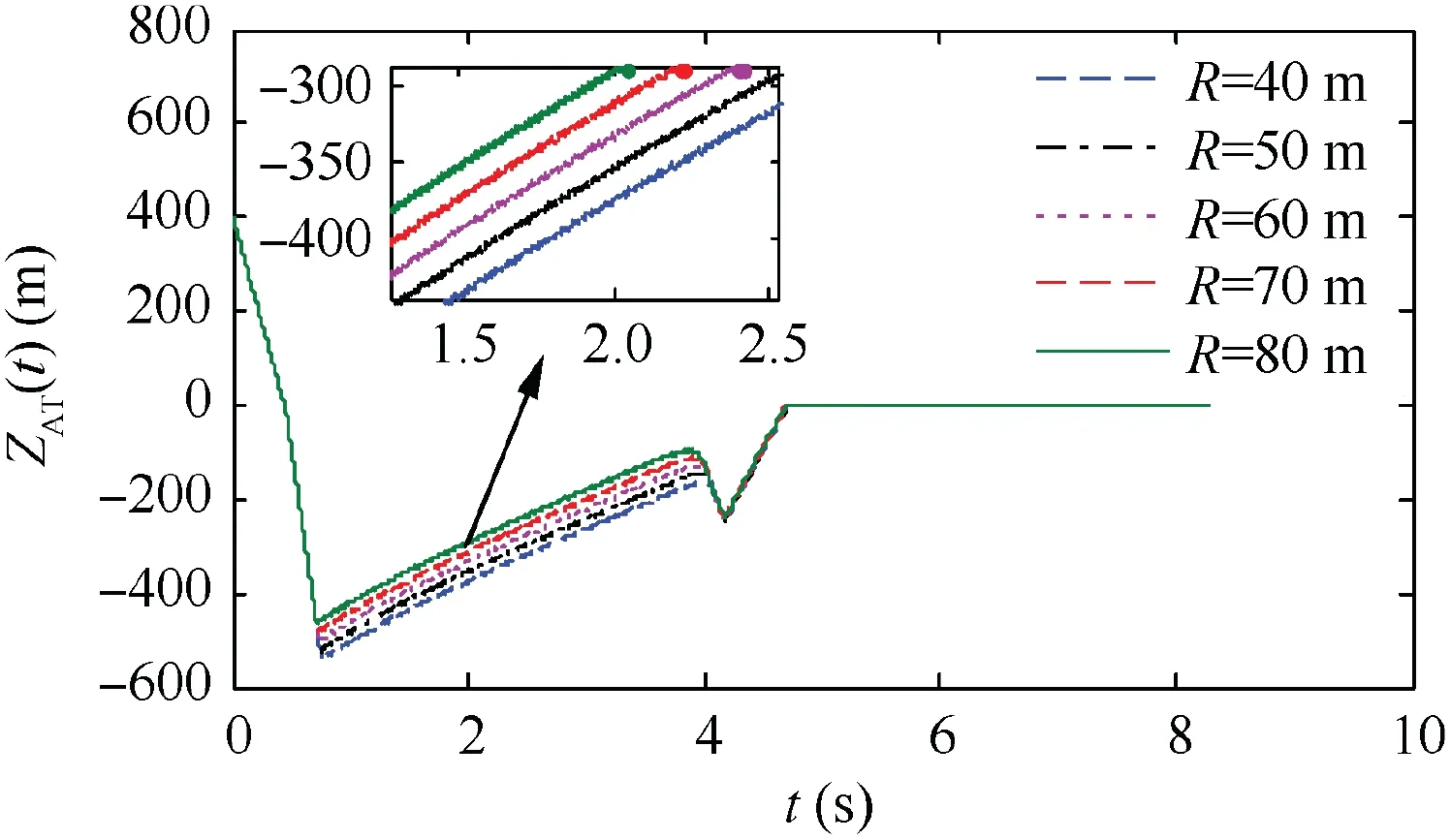
Fig. 14 Time evolutions of ZAT t( ) in Case 2 by using SSBGL with various values of R.
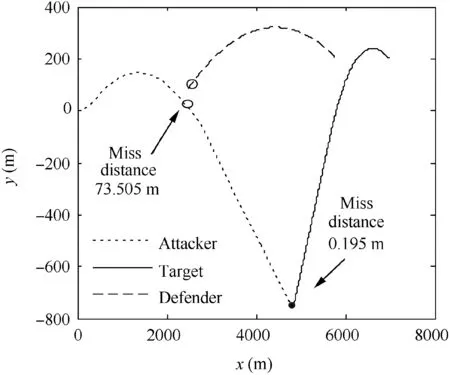
Fig. 15 Trajectories in Case 2 by using SSBGL.
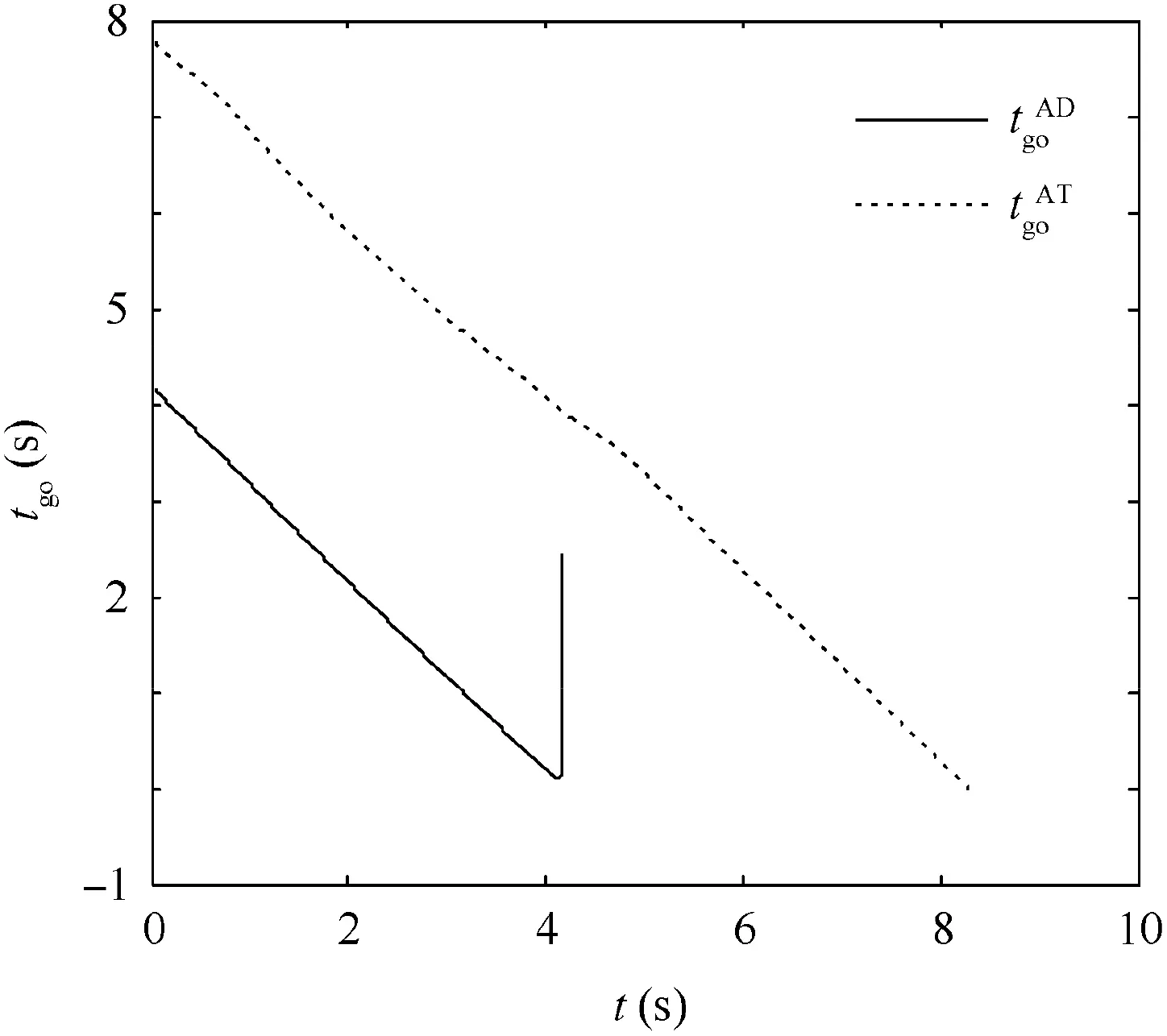
Fig. 16 Time-to-go in Case 2 by using SSBGL.
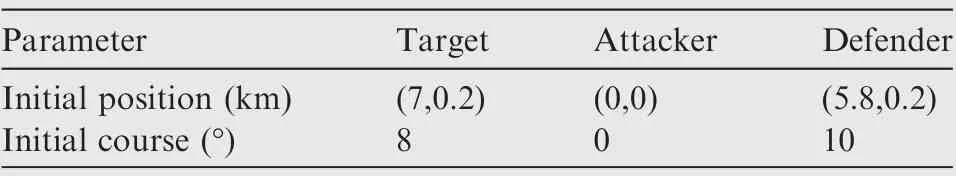
Table 3 Initial parameters for Case 3 by using SSBGL.
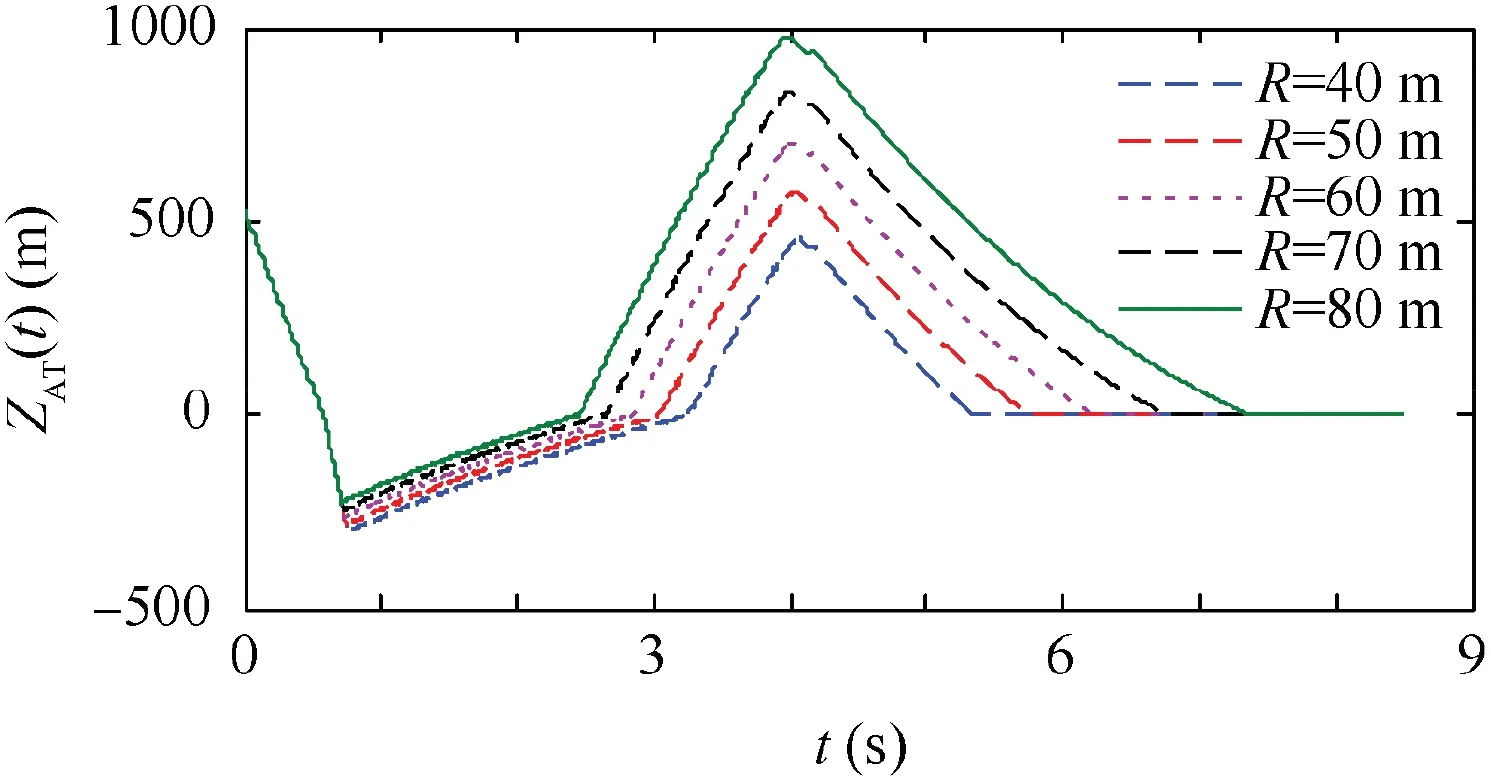
Fig.17 Time evolutions of ZAT t( )for Case 3 using SSBGL with various R.

Fig. 18 Trajectories in Case 3 using SSBGL.
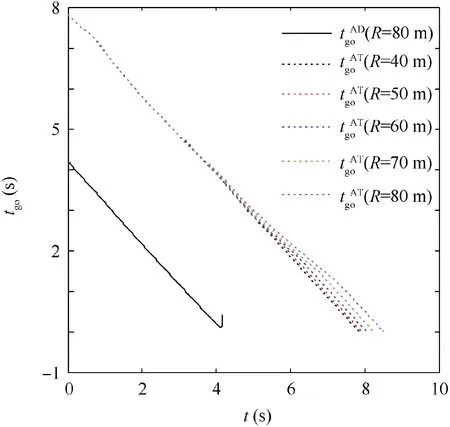
Fig. 19 Time-to-go in Case 3 using SSBGL.
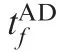
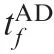
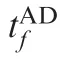
Table 4 Initial parameters for Case 1 by using OSBGL.

Fig. 20 Time evolution of ZEMs in Case 1 by using OSBGL with various values of R.
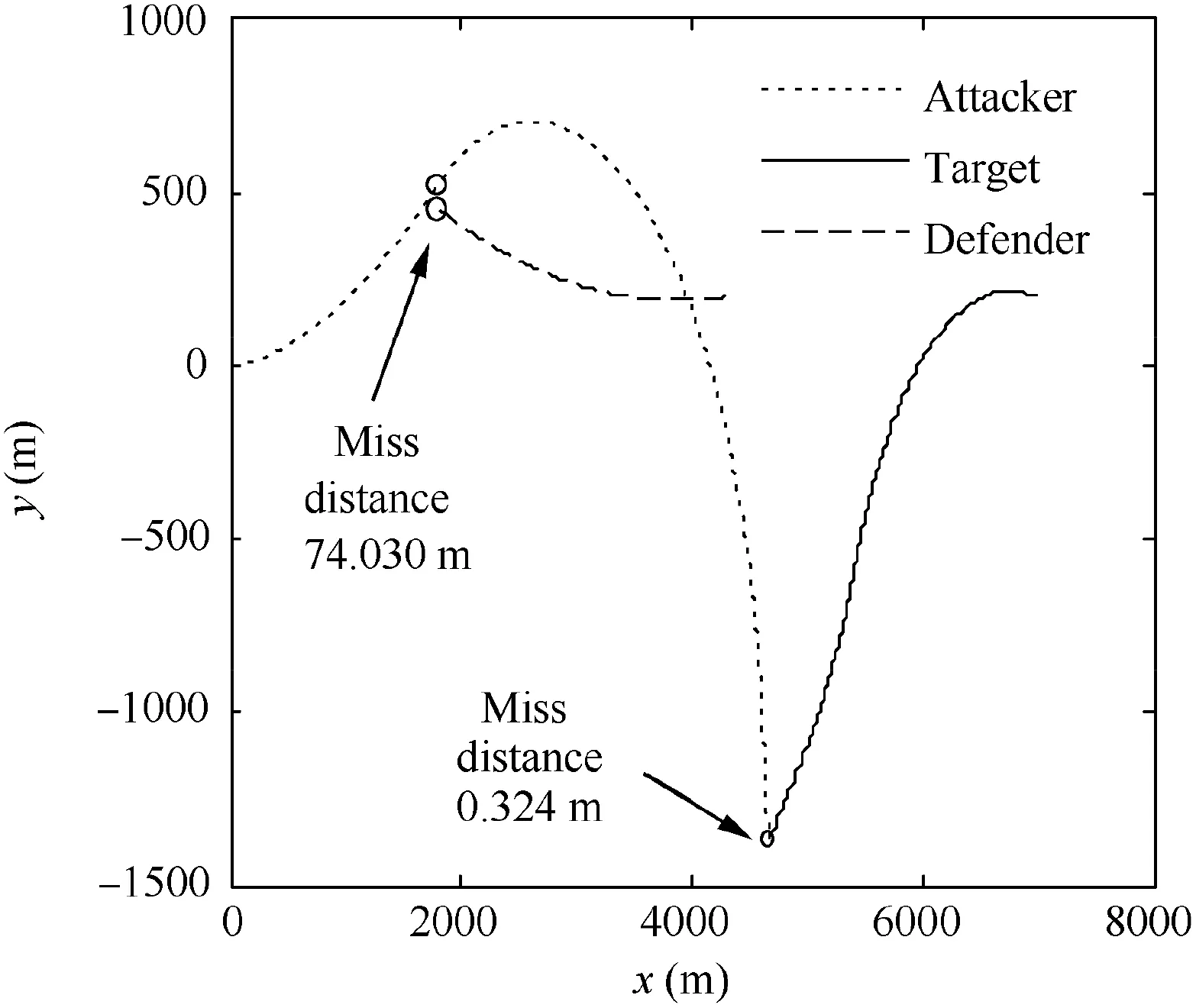
Fig. 21 Trajectories in Case 1 by using OSBGL.
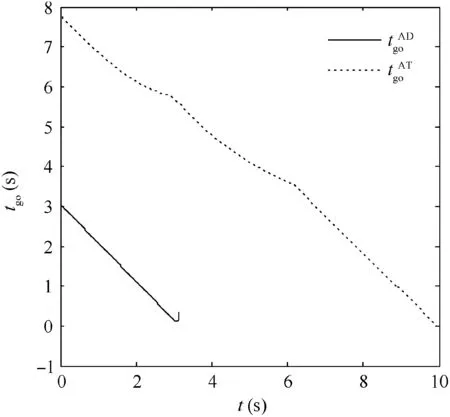
Fig. 22 Time-to-go in Case 1 by using OSBGL.
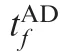
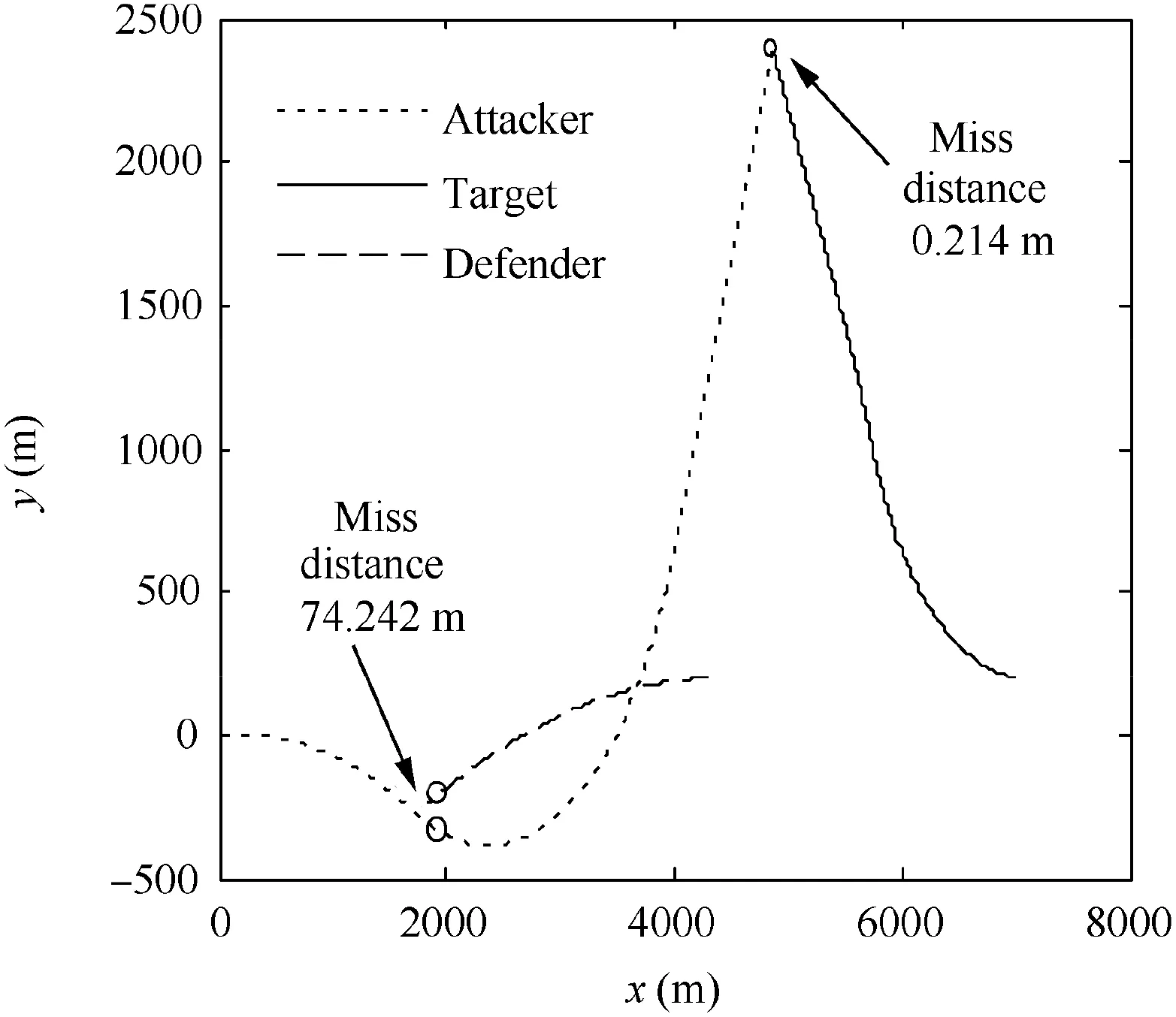
Fig. 23 Trajectories in Case 1 by using SSBGL.
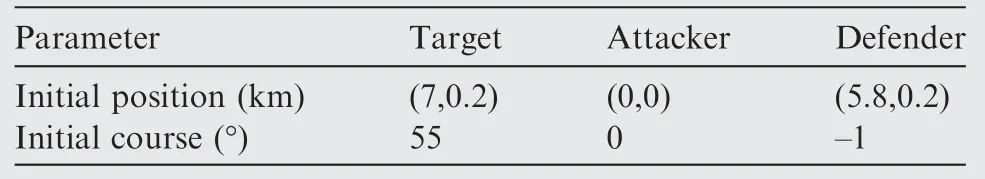
Table 5 Initial parameters for Case 2 by using OSBGL.
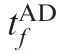
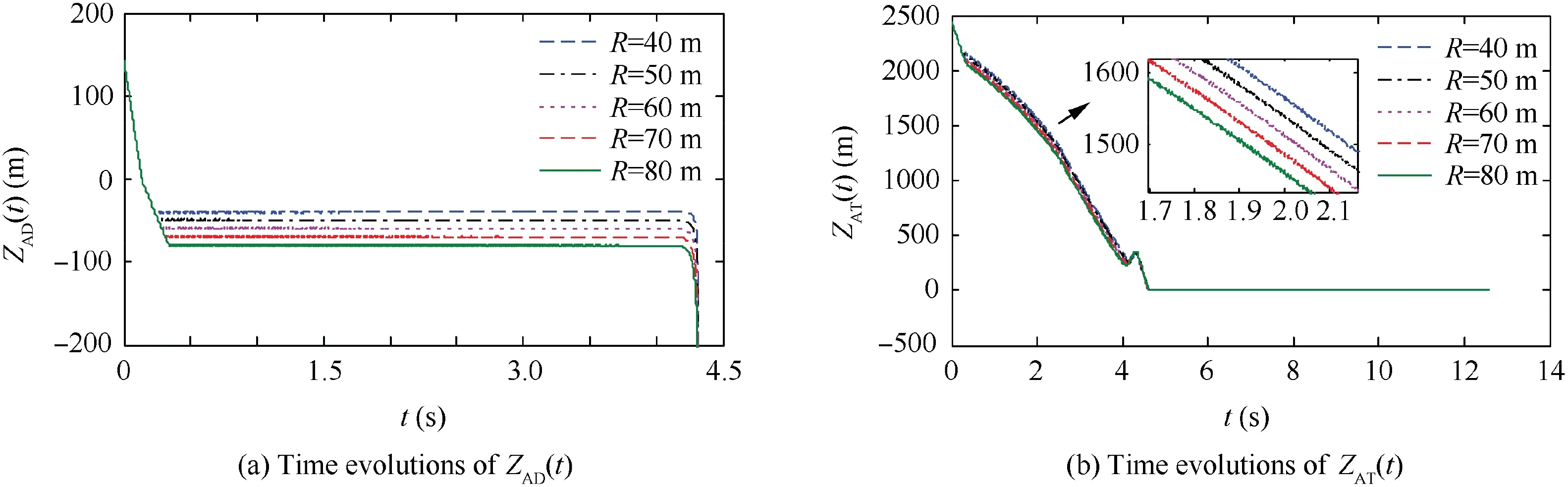
Fig. 24 Time evolution of ZEMs in Case 2 by using OSBGL with various values of R.
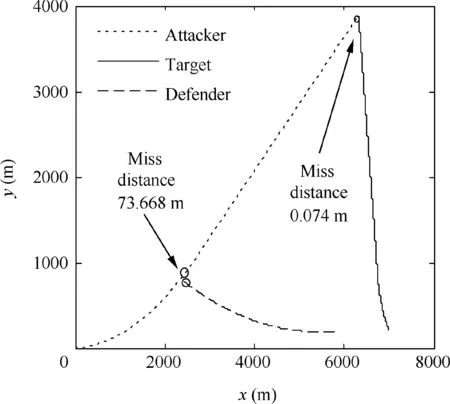
Fig. 25 Trajectories in Case 2 by using OSBGL.
Fig. 26 Time-to-go in Case 2 by using OSBGL.
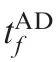
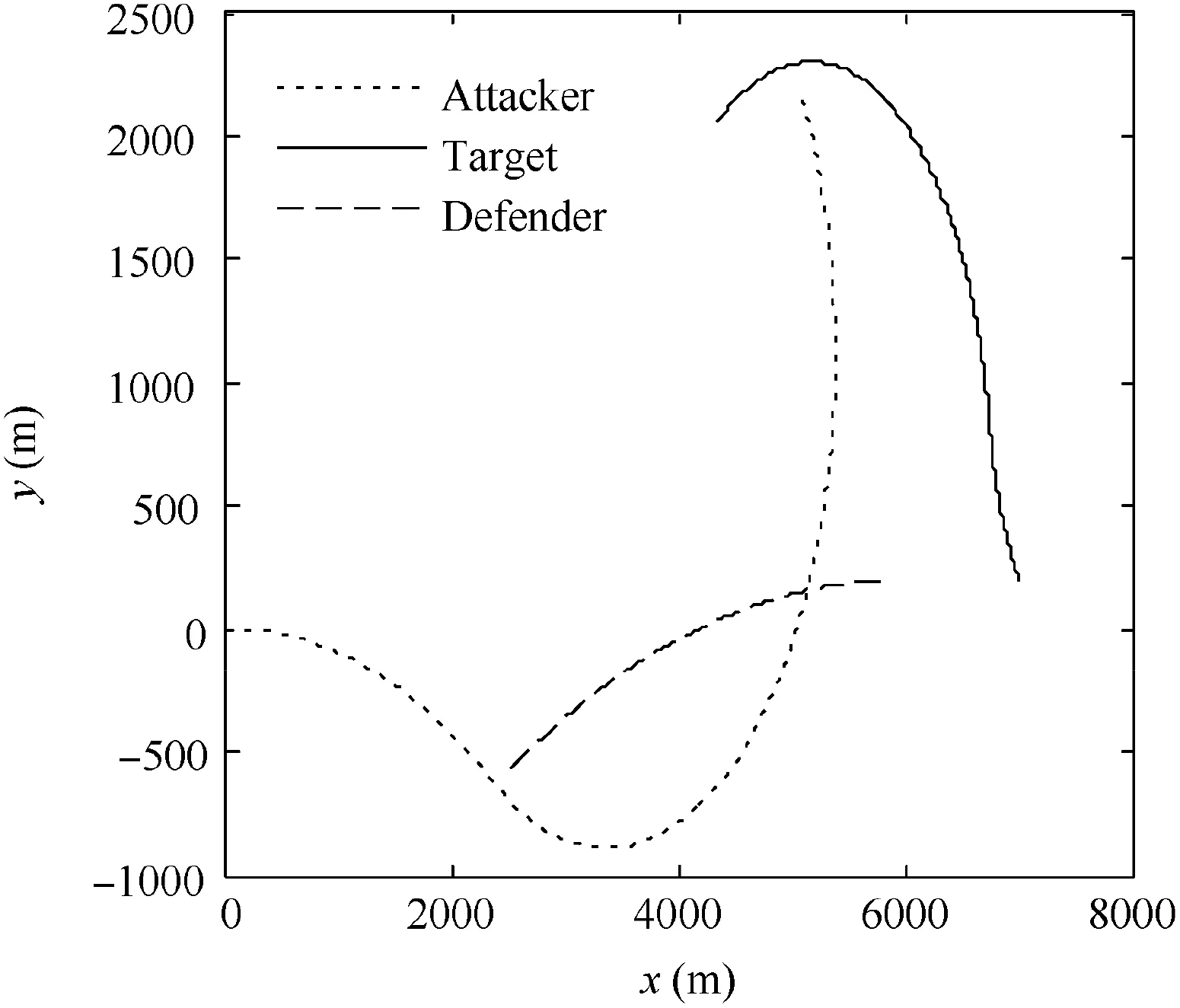
Fig. 27 Trajectories in Case 2 by using SSBGL.
Fig. 28 Trajectories in Case 2 by using EBPGL.
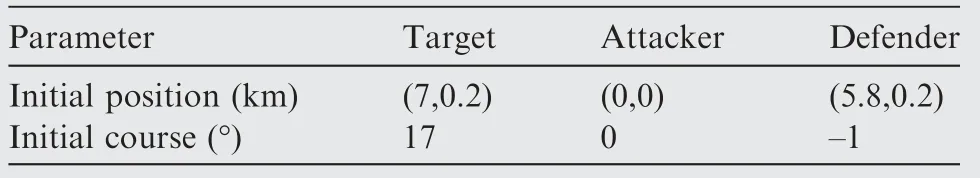
Table 6 Initial parameters for Case 3 by using OSBGL.

Fig.29 Time evolutions of ZAT t( )in Case 3 using OSBGL with various R.
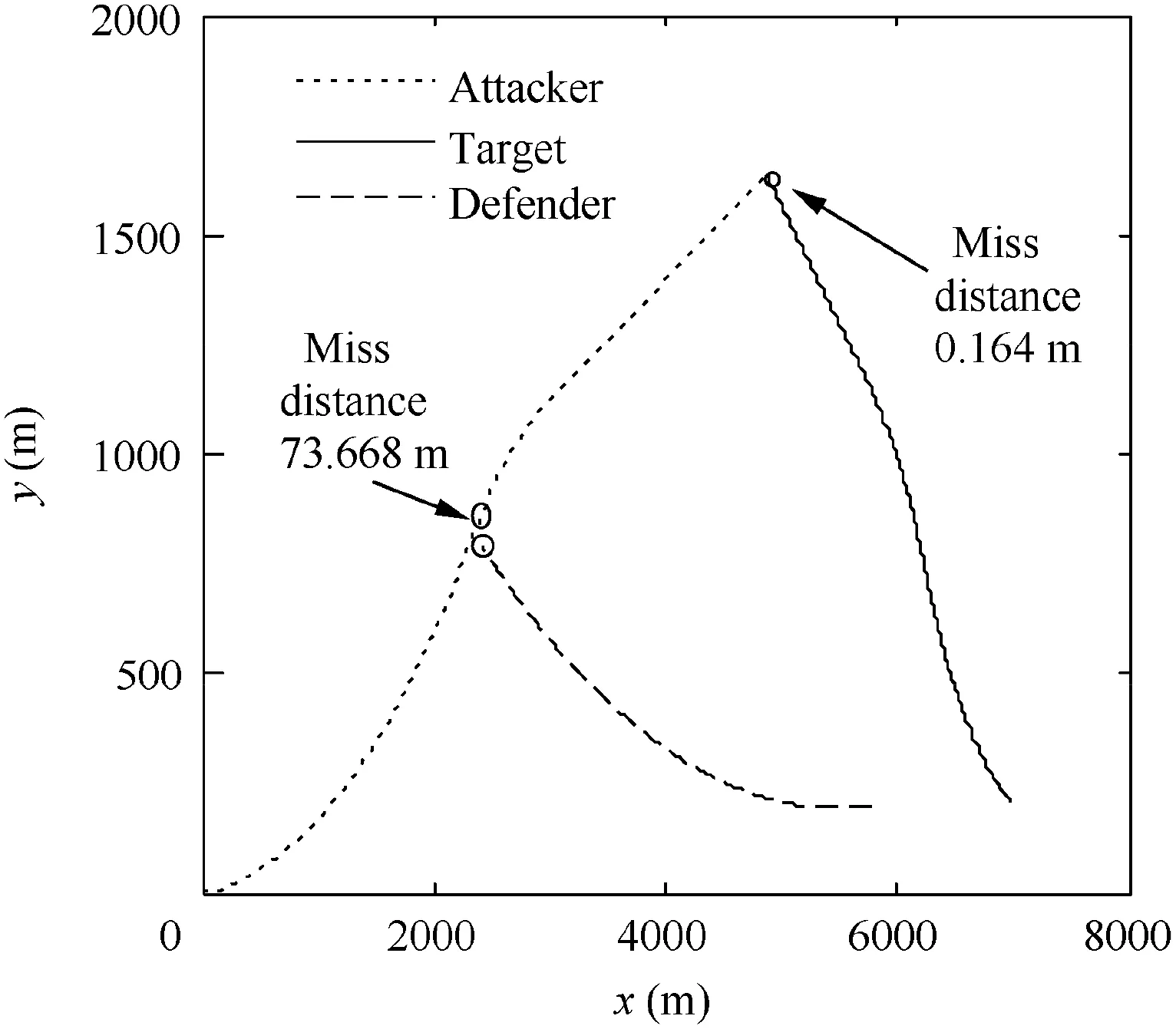
Fig. 30 Trajectories in Case 3 by using OSBGL.
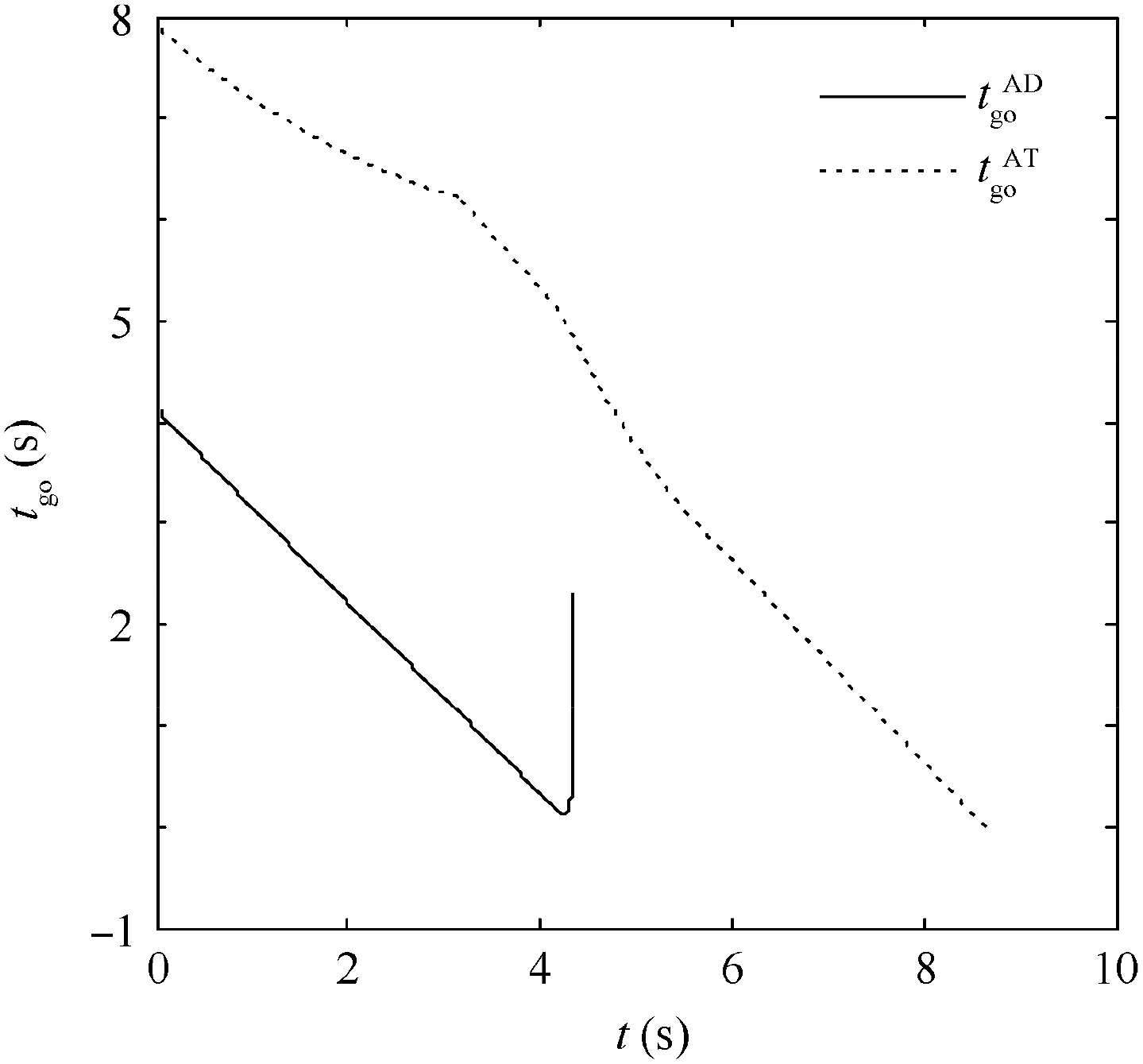
Fig. 31 Time-to-go in Case 3 by using OSBGL.
Fig. 32 shows the trajectories when the attacker uses SSBGL with a running time of 12 s. The attacker fails.Fig. 33 shows the trajectories when the attacker uses EBPGL guidance law with simulation running for 12 s. The attacker cannot hit the target.

Fig. 32 Trajectories in Case 3 by using SSBGL.
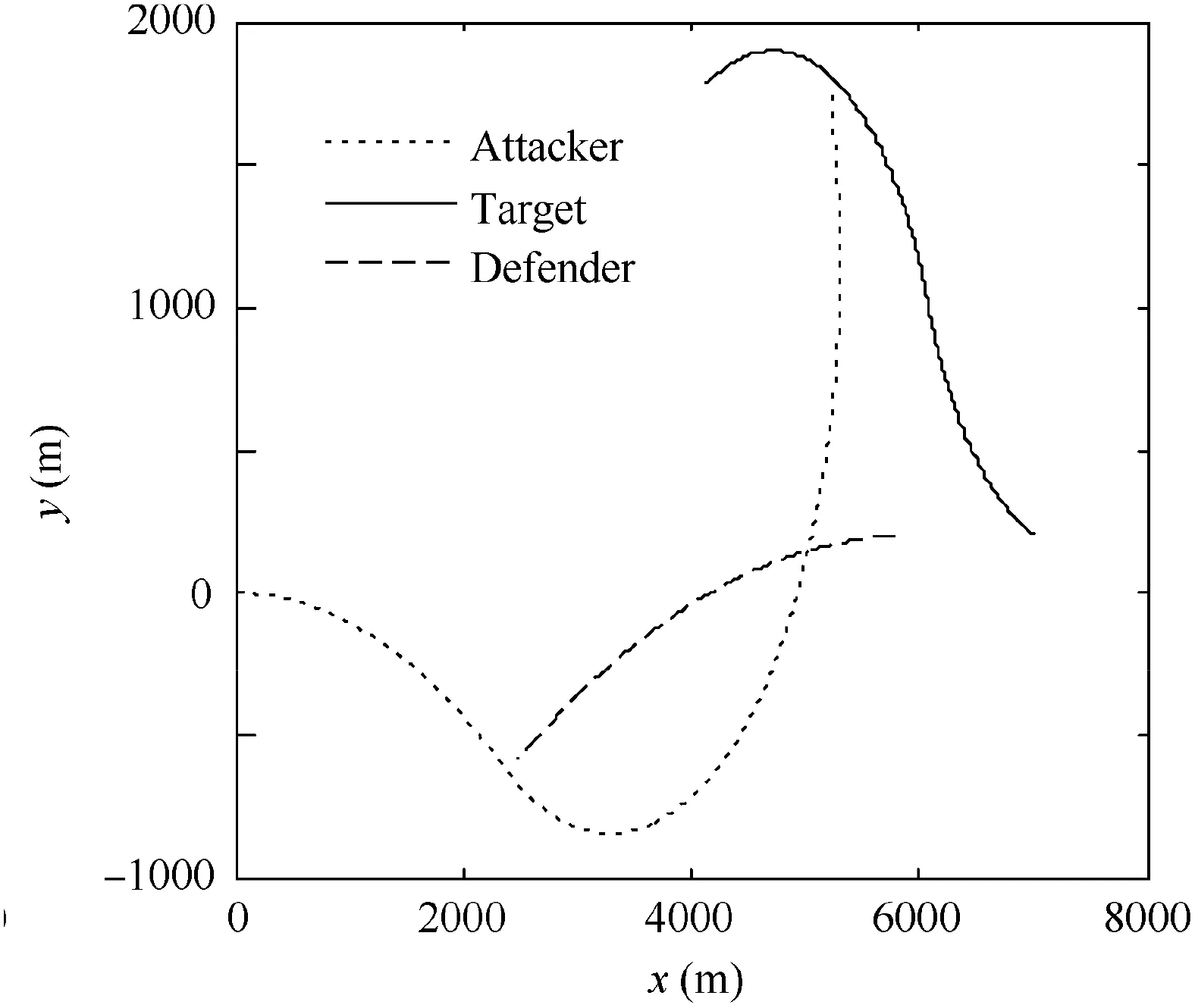
Fig. 33 Trajectories in Case 3 by using EBPGL.
5. Conclusions
Evasion and pursuit guidance laws for a missile attacking a defended aircraft are derived based on differential game theory. In this paper, two new guidance laws were proposed and sufficient conditions for the missile to succeed were analyzed by using the linear method. Although the actual feasible range of ZAT(t=0) deviates from the range calculated by the linear model,the range provided by the solution can be used as a reference.With the two guidance laws,it is not necessary for the attacker to know the control efforts of the defender and the target.However,the position and velocity of the defender and those of the target, which are easily measured by the attacker,need to be known by the attacker.
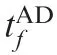
In future works, the nonlinear guidance law for attacking the defended aircraft will be investigated while taking noise sensitivity into consideration.
Acknowledgements
This work was co-supported by the National Natural Science Foundation of China (No.11672093) and the Shanghai Aerospace Science and Technology Innovation Foundation, China(No. SAST2016039).
 CHINESE JOURNAL OF AERONAUTICS2019年10期
CHINESE JOURNAL OF AERONAUTICS2019年10期
- CHINESE JOURNAL OF AERONAUTICS的其它文章
- Design and analysis of a hypersonic inlet with an integrated bump/forebody
- Experimental study of effect of post processing on fracture toughness and fatigue crack growth performance of selective laser melting Ti-6Al-4V
- Efficient and accurate online estimation algorithm for zero-effort-miss and time-to-go based on data driven method
- Experimental and numerical investigation of threedimensional vortex structures of a pitching airfoil at a transitional Reynolds number
- A methodology for simulating 2D shock-induced dynamic stall at flight test-based fluctuating freestream
- Robust adaptive compensation control for unmanned autonomous helicopter with input saturation and actuator faults
