Cloud Computing in Data Backup
Abstract:Cloud computing differs from traditional services in that it can be provided in an elastic manner. In addition, the cloud can serve anyone on the Internet or a limited number of users. Cloud computing has some unique advantages but another important feature is data backup. In this article, we focus on data backup in cloud computing, we will demonstrate the backup problem and make recommendations.
Key words: Cloud Computing, Data Backup, Security
1.Introduction
In the era of IT industries today, large-scale computing has been widely applied in many fields. People try to develop a more reliable, stable, convenient and safer operating system to accomplish it. The emergence of the Cloud computing system was a great response to this demand.
Cloud computing refers to the hosted services that are delivered over the Internet. Different from the conventional services, those on the Cloud can be offered in an elastic manner which means that customers can access as much as they need. Additionally, the Cloud can be public or private, that is, it supplies services for either anyone on the Internet or a limited number of users.
There are some unique advantages by using Cloud computing: more elastic hardware, the faster speed of transferring data, the lower power consumption and accessibility. But one more important feature is its data backup.
Data backup refers to the method of backing up data in case of a loss. It requires replication and archiving computer data so the case of data deletion or corruption can be easily solved.
2.Background
Cloud has sufficient capacity to store large amounts of data for various clients with complete security on a server in a professional data center. The data center has systems that detect smoke, suppress fires and provide emergency power to protect the data. The location of these data centers are secret and heavily guarded and reinforced to prevent disasters or intruders to physically harm and steal storage hardware. Data that were private and important uploaded by users in the cloud were encrypted for both users protection and the cloud computing agency. When the backup solution was provided through the cloud, a completely continuous backup will ensure that there will be no loss from the moment an error occurred. Backup off-site will ensure important data backed up will not be lost in natural disasters such as theft, fire or flood. Therefore, the need of backup techniques arises.
Offsite data backup refers to storing important data on a server through the Internet, while onsite storage refers to storing data on local storage devices such as hard drives, DVDs or CDs. Onsite storage has immediate access to data and does not need the Internet. However, although onsite storage is less expensive, it can be destroyed by natural disasters. For the offsite storage, it has to connect to the Internet to access the data in it from any location and the backed-up data can be shared with different remote locations.
There are multiple-choice and ways to off-site backup and cloud backup serve as the off-site facility. Firstly, directly back up to the public cloud. Organization resources were stored by copying resources to the public cloud. The backup software was not specifically provided but the destination and safekeeping for the data were provided by the cloud service. Secondly, backing up to a service provider. The organization uses provided backup software or application by the service to write data to the cloud service provider. Thirdly, choosing a cloud-to-cloud (C2C) backup. Cloud-to-cloud backup means backing up data from one cloud to another cloud. Normally, C2C service hosts the software that handles this process. Last but not least, using online cloud backup systems. Backing up data to a cloud backup service by hardware alternatives that are almost as plug and play as backup. These devices are all-in-one backup machines, including backup software and disk capacity. These devices also keep the latest local backup other than backing them up to a cloud backup provider. (A smart data backup technique for cloud computing using seed block algorithm strategy, 2015)
In the cloud, to keep the data safe, data encryption works with public-key encryption that combines several cryptographic keys. For example, a users computer owns one unique public key and one completely private key. The public key is available for other computers that wanted to send files to the user. The other computer will encrypt their file with a symmetric key and place both into a file that is encrypted by the users public key. Then, the file is transferred. For decryption, the users private key decrypts the file and receive the file and symmetric key sent by the other computer. Lastly, the file is decrypted and the content of the file is unlocked. ("Cloud storage: What is it and how does it work?", 2019)
3.Issues
3.1 Data Security
As Cloud computing involves sharing of computing resources there are a large number of users that share the same storage and other computing resources. And most data will move across the public internet on its way to the cloud. Therefore the data should be fully protected such no other user on the cloud can access your important and useful data and makes some modification or any election. When using cloud storage, data is moved outside of an outside organizations building and into the control of an outside provider. Therefore the cloud backup providers equipment, physical security procedures, data protection process and fiscal viability are also important to data security. (A smart data backup technique for cloud computing using seed block algorithm strategy, 2015)
3.2 Appropriate Timing
For backup, its speed depends on bandwidth and latency. For example, when many organizations used internet connection at the same time, the backup could be slower. This could be bothersome when backing data up, but could be an even greater issue when it is necessary to recover data from the service.
For data recovery, there must be transfer of server to the cloud. The relocation of server means to remove the main servers data to another server. The process of data recovery takes some time for retrieval of data from the remote repository as this remote repository is far away from the main cloud and its user. Therefore, the time taken for such a retrieval must be minimum as possible such that the user can get the data as soon as possible without concerning the fact that remote repository is how far away from the user. (A smart data backup technique for cloud computing using seed block algorithm strategy, 2015)
3.3 Cost-effectiveness
The cost of establishing the remote setup and for implementing its technique must be minimum. Because the cost will escalate when backing up a large amount of data to the cloud. This kind of cost cannot be reduced. The cost for the execution of remote servers and its recovery and backup technique also plays an important role while creating the structure for the main cloud and its reporter remote cloud. (International Journal of Trend in Scientific Research and Development, 2018)
4.Flowchart
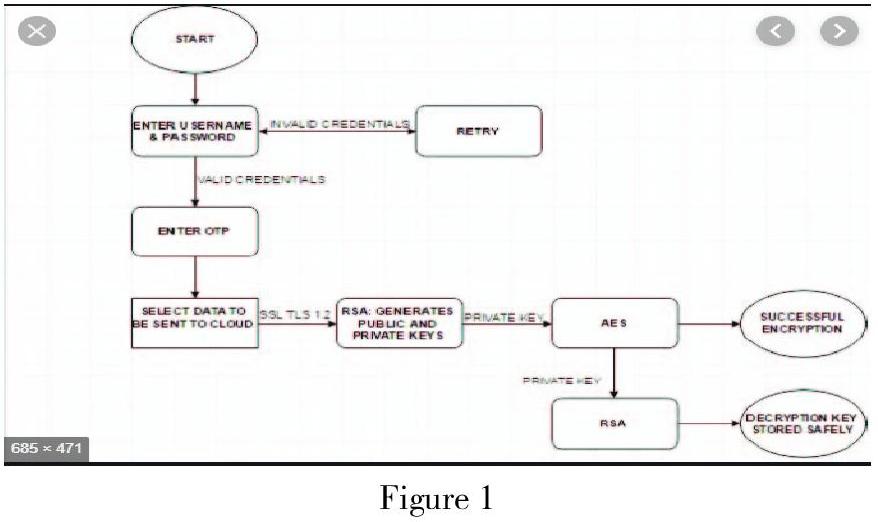
Figure 1
Figure 1 (2017) is a flowchart that shows how the cloud ecosystem for data security and privacy. First, the users enter their name and password, if the input is invalid credentials then the input requirement will be asked again, else go into the next step to enter the one-time password (OTP). After that, the cloud system selects data which will be sent to the cloud. Referred to the SSL and TLS, the cloud use RSA algorithm to generate public and private keys. Finally, by the private key, the cloud system uses AES to get successful encryption while by the private key, RSA method is adopted and the decryption key will be stored safely.
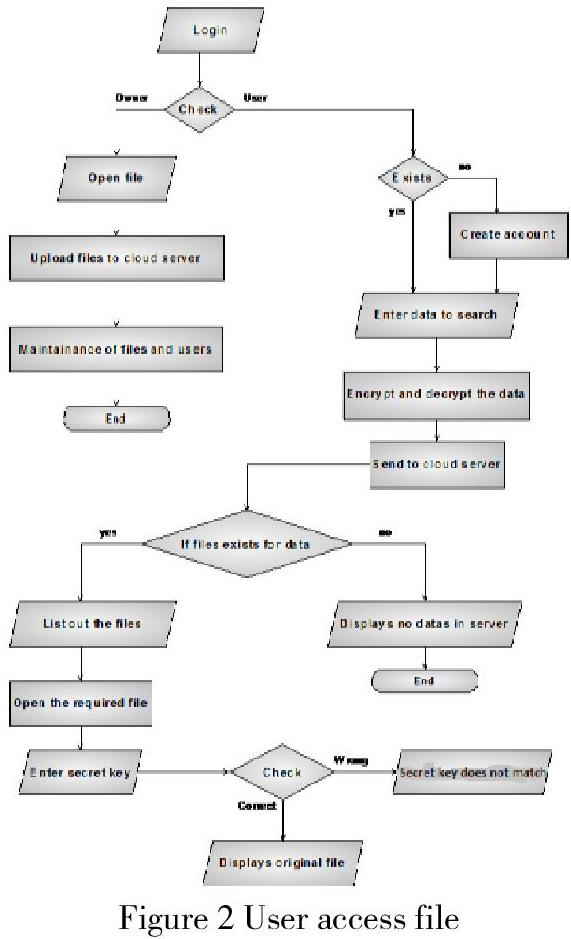
Figure 2 User access file
In Figure 2 (2013), when the user login the cloud computing system, his identity information will be verified. The owner of the file can open the file and upload it to the cloud server also maintaining the files and users. A user can choose to create an account if no account exists or directly enter data to search. Then encrypt and decrypt the data and send it to the cloud server. If the files exist for data, then list out the files, open the required file and enter the secret key, after checking, the user can access the original file. If the files do not exist for data, will display no details in the server.
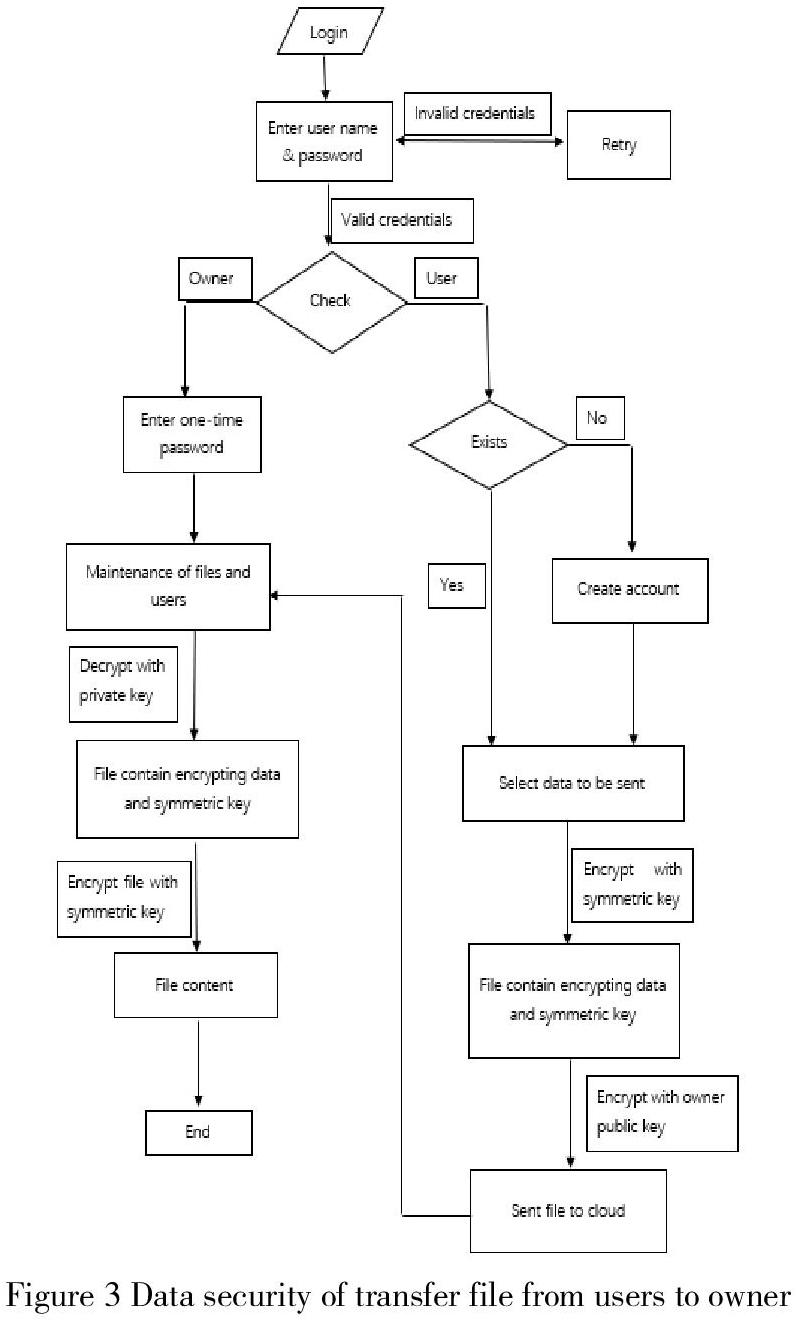
Figure 3 Data security of transfer file from users to owner
By referencing Figure 1 and Figure 2, Figure 3 is a flowchart that shows how users send files to the owner. After entering username and password, if both username and password match, it proceeds to check whether it is an owner or user. The owner will enter One Time Password and own a public key and a private key. The public key can be obtained by the users and produce a symmetric key to encrypt the file and the private key is only available for the owner. The file encrypted by the owners public key with file and symmetric in it was sent to the cloud. From the cloud, the owner can access the file and decrypt it using the owners private key to get the content of the file.
5.Recommendation
After the maintenance of files and users, data backup could be added. The reason for adding the data backup is that we need to prevent from data loss after the maintenance of files and users. In addition, since data backup requires replication and archiving computer data, it is more convenient for users to operate their data like deletion, corruption or adding.
By cloud-to-cloud backup, the data in the cloud is backed up to another cloud. This adds an extra layer of protection for the owner from cyber-attack, accidental deletion or data corruption. After users send the encrypted files to the owner, all new added files and users information should be back up to the cloud. When backing up using cloud-to-cloud backup, all the data should be encrypted by the public key of the owner or generate an OTP for the owner to access the data. These can increase the data security of the owner as other than the owner itself, no one can access the backup unless login as owner and enter the OTP.
When sending files to the cloud, user may choose to move it to the public cloud. Public cloud is anyone who wants to use or purchase them can access it. So, for the public cloud, security is very important. Provider can divide public cloud into several cloud silos. Only the specific user can access cloud silos. When a new user creates an account, he or she will get his or her own cloud silos. Later only the user who enter both the correct username and password can access this siol.
While security concerns have been raised over public cloud environments, when implemented correctly, the public cloud can be as secure as the most effectively managed private cloud implementation if the provider uses proper security methods, such as intrusion detection and prevention systems (IDPs).
6.Conclusion
In conclusion, there is no doubt that cloud computing is a powerful technique for dealing with computer data entered by the users. It provides either a public or private storage space to store and operate data information, speeds up the method of transferring data, supports accessibility and a higher level of security for reading and using data.?However, the most important one is the data backup since its function is to prevent the case of data loss.
In the researching process, there are three main issues about data backup: data security, appropriate timing and cost-effectiveness. Compared and referred to the conventional cloud computing system, we come up with the new one of cloud computing system and do some recommendations based on that. The mainly recommended part is to add the data backup section which contains adopting a new method called cloud-to-cloud and speeding up backup process.
Cloud-to-cloud method generates a better protection for users from the external interruption. Additionally, it also uses the public key to encrypt and provides OTP to access data. These measures greatly contribute to a higher level of security of data information. Meanwhile, another method called public cloud silos also plays such function. Cloud silos has double checking: username and password. It aims to ensure and identify the correct user to access data so that the private data information will not be attacked or modified in the public cloud.
From this research, we learned a lot about the cloud computing system. Especially from the flowchart part, we clearly had a better understanding about the elements, structure and the principle of the cloud system. As for our main object data backup, we knew that the great importance of data security, data storage and data protection. Data backup plays a vital role in any system and its function should not be ignored.
References
[1] L. Zhao, S. Sakr, A. Liu, and A. Bouguettaya, Cloud data management. 2014.
[2] V. Mosco, To the cloud: Big data in a turbulent world. 2015.
[3] V. Lakshmanan, Data Science on the Google Cloud Platform: Implementing Real-Time Data Pipelines - from Ingest to Machine Learning. 2018.
[4] R. (Roger C. T. Lee, Big data, cloud computing, data science & engineering.
[5] S. Nelson, Pro Data Backup and Recovery. 2011.
[6] A. Arora, A. Khanna, A. Rastogi, and A. Agarwal, “Cloud security ecosystem for data security and privacy,” in Proceedings of the 7th International Conference Confluence 2017 on Cloud Computing, Data Science and Engineering, 2017, pp. 288–292.
[7] G. S. Narke, “A smart data backup technique for cloud computing using seed block algorithm strategy,” Int. Res. J. Eng. Technol., pp. 807–813, 2015.
[8] “(PDF) Cloud Computing in Data Backup and Data Recovery | International Journal of Trend in Scientific Research and Development - IJTSRD-Academia.edu.”[Online].Available: https://www.academia.edu/
37833034/Cloud_Computing_in_Data_Backup_and_Data_Recovery. [Accessed: 07-Dec-2019].
[9] Team, “Cloud storage: What is it and how does it work? – How It Works,”2016.[Online].Available: https://www.howitworksdaily.com/
cloud-storage-what-is-it-and-how-does-it-work/.[Accessed: 07-Dec-2019].
[10] V. GR and A. Reddy, “Data Security in Cloud based on Trusted Computing Environment,” doaj.org, no. 1, pp. 187–191, 2013.
作者簡介:趙思婕(?1998年12月28)女,漢,河北省石家莊人,?廈門大學本科三年級在讀,?研究方向:計算機
(廈門大學馬來西亞分校?馬來西亞?43900)

